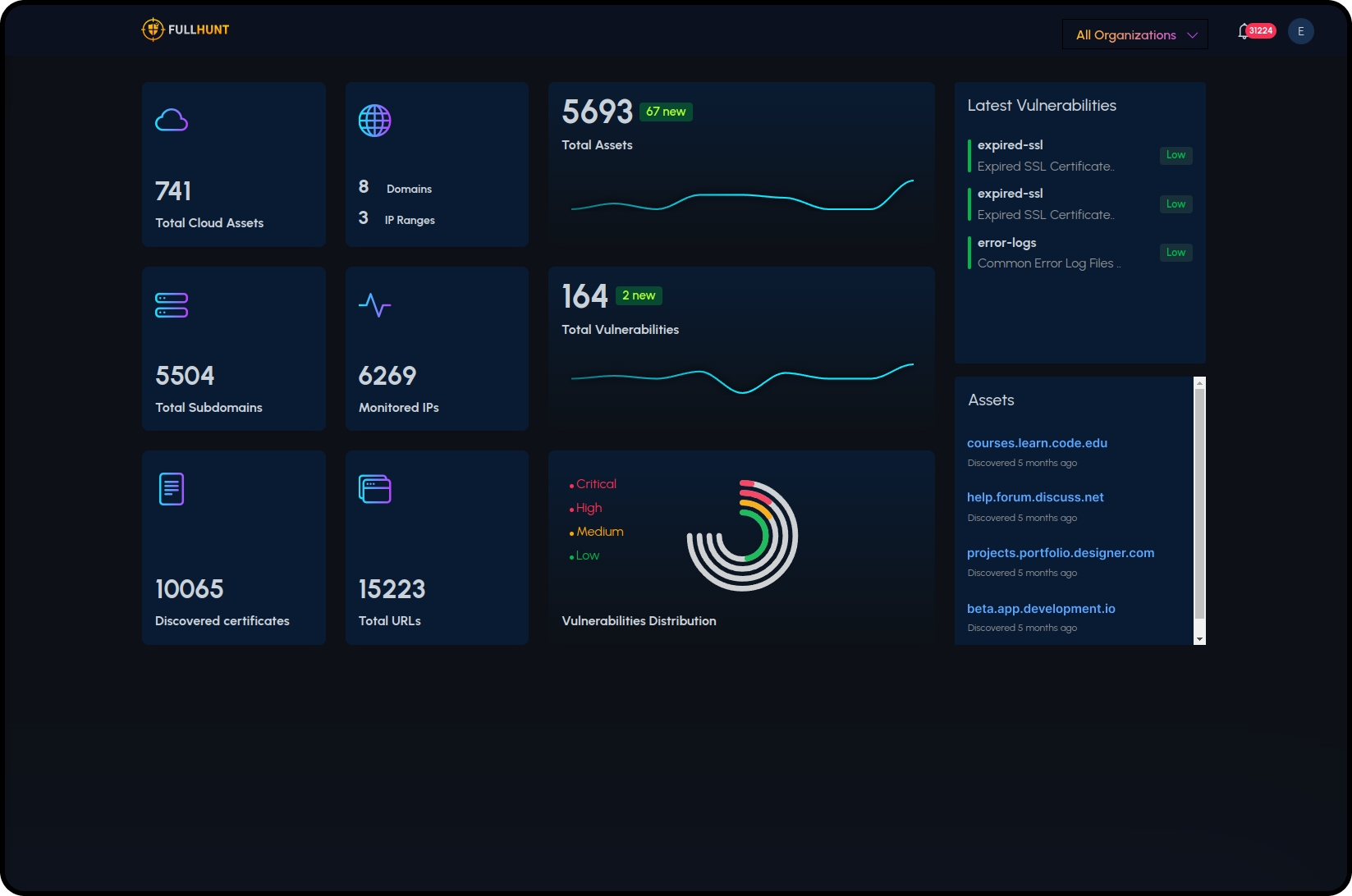
Know every external asset.Fix what's exploitable.
FullHunt maps your internet-facing footprint in real time, monitors it for change, validates vulnerabilities, and enriches them with exploit intelligence-so you can reduce risk without the noise.
Expose Your Attack Surface
Discover internet-facing assets in seconds with FullHunt's search engine

Complete Attack Surface Protection in 4 Steps
From discovery to real-time alerting, FullHunt provides continuous attack surface management that scales with your organization.
Discover
Cloud-distributed engines automatically discover and map your entire external attack surface in minutes, including domains, subdomains, IPs, and cloud assets.
Monitor
24/7 continuous monitoring tracks every change across your attack surface, detecting new assets, configuration drifts, and potential exposures in real-time.
Detect
Automated scanning identifies thousands of vulnerabilities across your assets, with runtime validation ensuring zero false positives and accurate risk assessment.
Alert
Instant notifications through your preferred channels (Slack, Teams, SIEM) whenever critical risks or exposures are identified, enabling immediate response.
The Solution
You cannot protect what you do not know about. Without clear visibility, no security control can be established correctly.

Exposure Understanding
Instantly understand your exposure and security risks, and drastically improve your security program with less effort and cost. Proactively identify your external attack surface with minimal configuration needed.

Large Attack Surface Database
FullHunt maintains one of the largest attack surface database of the entire Internet.


Comprehensive Suite
Offers a suite of External Attack Surface Management products and services to cover a wide range of use cases.

Zero Configuration
FullHunt automatically discovers your external attack surface, no configuration is needed.
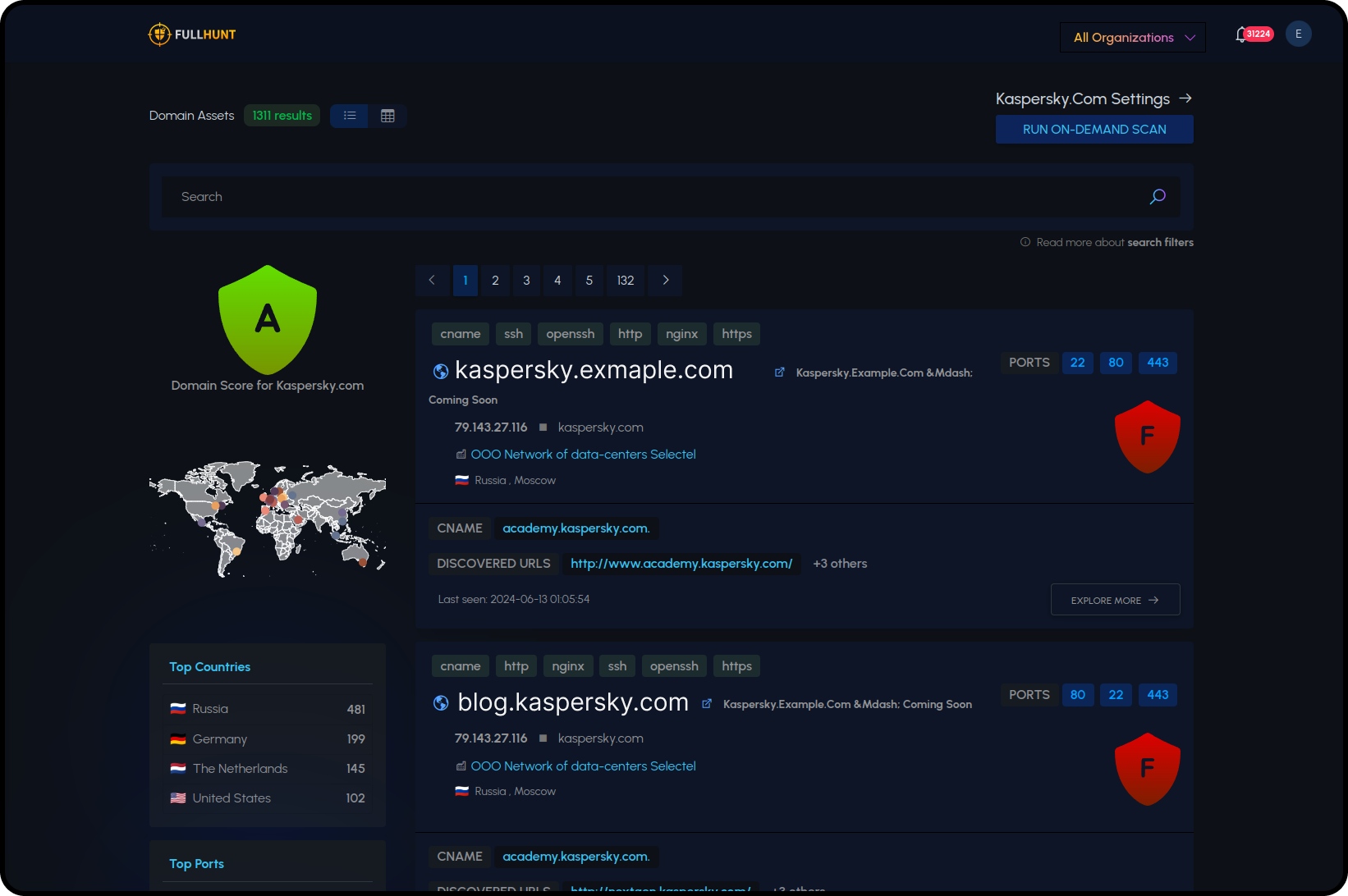
Why Teams Choose FullHunt
Live Coverage
External assets and exposure are tracked continuously, not snapshots.
Vulnerability Intelligence
Advanced vulnerability intelligence with curated security research helps prioritize what to fix now.
Zero-Config Onboarding
Be operational fast; enterprise roll-outs in minutes.
APIs + OEM
Build on top of our datasets and engines with enterprise & OEM APIs.
Built to Integrate & OEM
FullHunt is open by design. Stream findings into SIEM and SOAR, enrich tickets automatically, or build custom workflows on top of our APIs.
Security vendors can embed discovery, monitoring, and intelligence in their products without building scanning infrastructure. White-label and licensing options included.
Native Integrations
Connect to Splunk, XSOAR, FortiSOAR, Jira, Slack, and more with pre-built integrations.
Comprehensive APIs
Full REST API access for custom workflows, automation, and data enrichment.
Agentic AI with MCP
Connect AI agents to FullHunt's attack surface intelligence via Model Context Protocol for real-time threat analysis.
OEM & White-Label
Embed FullHunt capabilities in your product under your brand.
Constantly Evolving Intelligence
Our detection capabilities grow every day to keep pace with the evolving threat landscape
Rapidly expanding coverage; continuously updated
Growing detection library, always up-to-date
Comprehensive exploit database updated in real-time
Vulnerability Intelligence
Advanced vulnerability intelligence with curated security research and real-time exploit tracking, delivered to console and APIs
Complete Platform for Attack Surface Security
Discover, Monitor, Detect, and Alert-all in one platform

Internet-Scale Discovery
Map every external-facing asset including shadow IT and cloud services with continuous discovery.

Continuous Monitoring
Track changes, new services, and configuration drift in real time with automated alerts.

High-Fidelity Scanning
Validate thousands of vulnerability checks with runtime validation to reduce false positives.

Vulnerability Intelligence
Advanced vulnerability intelligence, curated security research, and real-time exploit tracking help you prioritize critical threats and accelerate remediation.

Dark Web Monitoring
Detect typosquatting, phishing, compromised credentials, and data leaks early.

Third-Party Risk
Extend visibility to vendors and subsidiaries with scoped monitoring and reporting.
Choose Your Path to Value
Get started with the option that fits your needs
Trusted by Security Teams Worldwide
Built for scale, security, and reliability
Enterprise-Grade
SSO, RBAC, and data encryption built-in for maximum security
Fast Onboarding
Get operational in under 30 minutes with zero infrastructure setup
Continuous Updates
Platform evolves with new features, vulnerability checks, and threat intelligence
Expert Support
Dedicated security experts available 24/7 to support your team

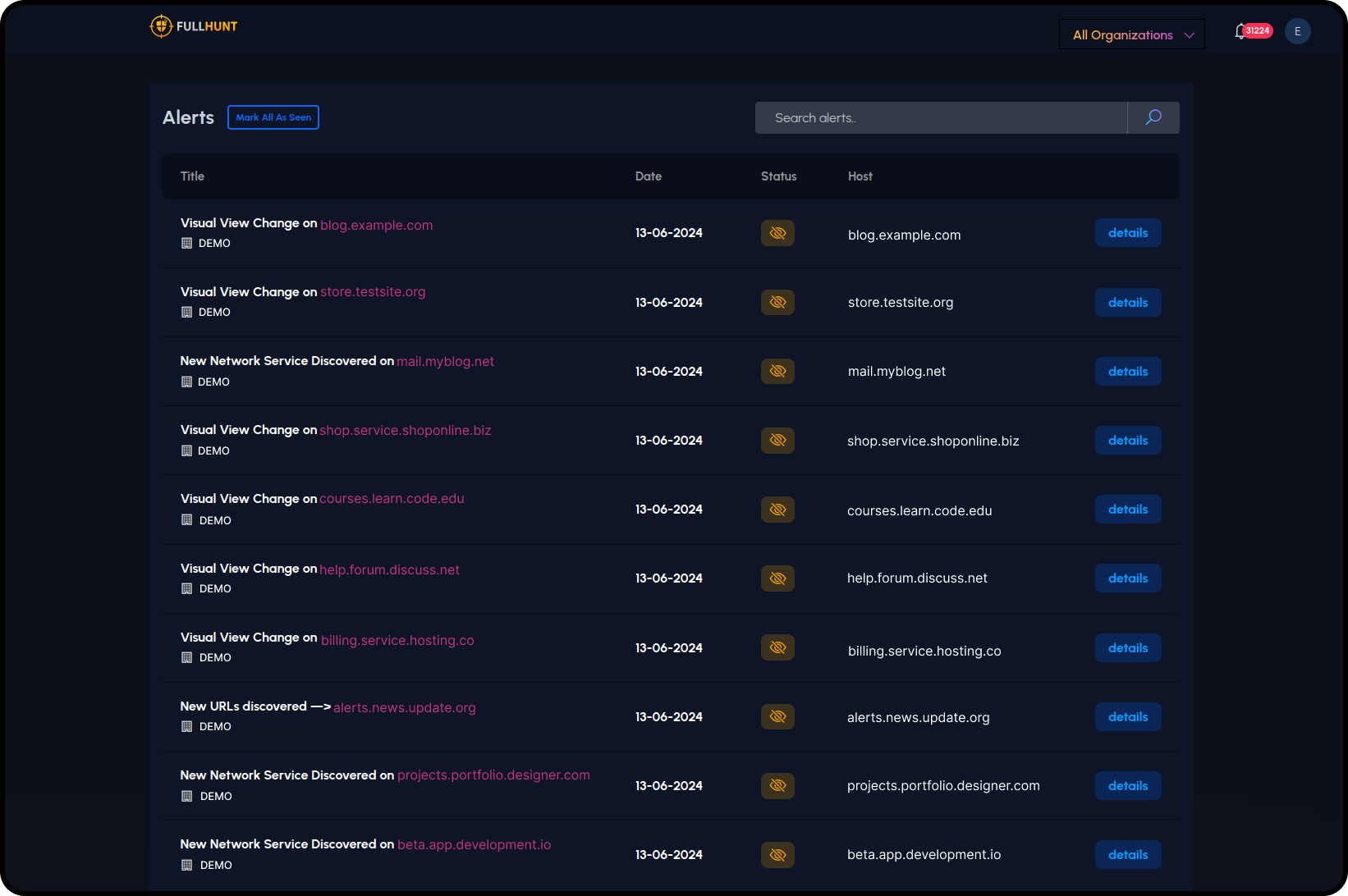
The First-Ever External Assets Monitoring Technology
FullHunt built the first enterprise-level framework for monitoring the External Attack Surface for changes and exposure. The framework has been evolving over the years to provide accurate intelligence to organizations worldwide.
Solving Attack Surface Management at Scale

The Start
FullHunt started as a project to solve a security challenge that all companies face today: Understanding the current exposure and performing continuous monitoring.
The Growth
FullHunt grew from a community project to become one of the leading Attack Surface Management platforms in the market.

The Expand
FullHunt now provides a suite of products to help build and mature your security program, including Continuous Attack Surface Management, DarkWeb Monitoring, Third Party Risk Management, Data Intelligence APIs, and Global Internet Space Scanning. Everything is powered by the FullHunt technology.


FullHunt Integrates With All Workflows And Playbooks
FullHunt provides a comprehensive set of APIs and integrations to help you automate your security workflows and playbooks.
Use some of the following integrations natively within the FullHunt Platform
Modern Continuous Security at scale
Choose the platform that fits your needs, from free community tools to enterprise-grade security.

FullHunt Community Platform
Basic Discovery is used by Security researchers and professionals for initial discovery. Free for everyone, forever.
Get Started
FullHunt Enterprise Platform
The Complete Attack Surface Management Platform. Used by Security teams for Continuous Discovery, Monitoring, and Vulnerability Scanning at scale.
Get StartedReady to expose your attack surface?
Join security teams using FullHunt to discover, monitor, and secure their external infrastructure.






