Expose Your Attack Surface
We Redefine Attack Surface Management
If you don't know all your internet-facing assets, and which ones are vulnerable, FullHunt is here for you. FullHunt identifies and secures your External Attack Surface.
Expose your attack surface
What is FullHunt?
Automated Offensive Security Platform
FullHunt an Attack Surface Management platform that enables companies to continuously discover, monitor, and secure the External Attack Surface and Internet-facing assets.

The Solution
You cannot protect what you do not know about. Without clear visibility, no security control can be established correctly.

Exposure Understanding
Instantly understand your exposure and security risks, and drastically improve your security program with less effort and cost. Proactively identify your external attack surface with minimal configuration needed.
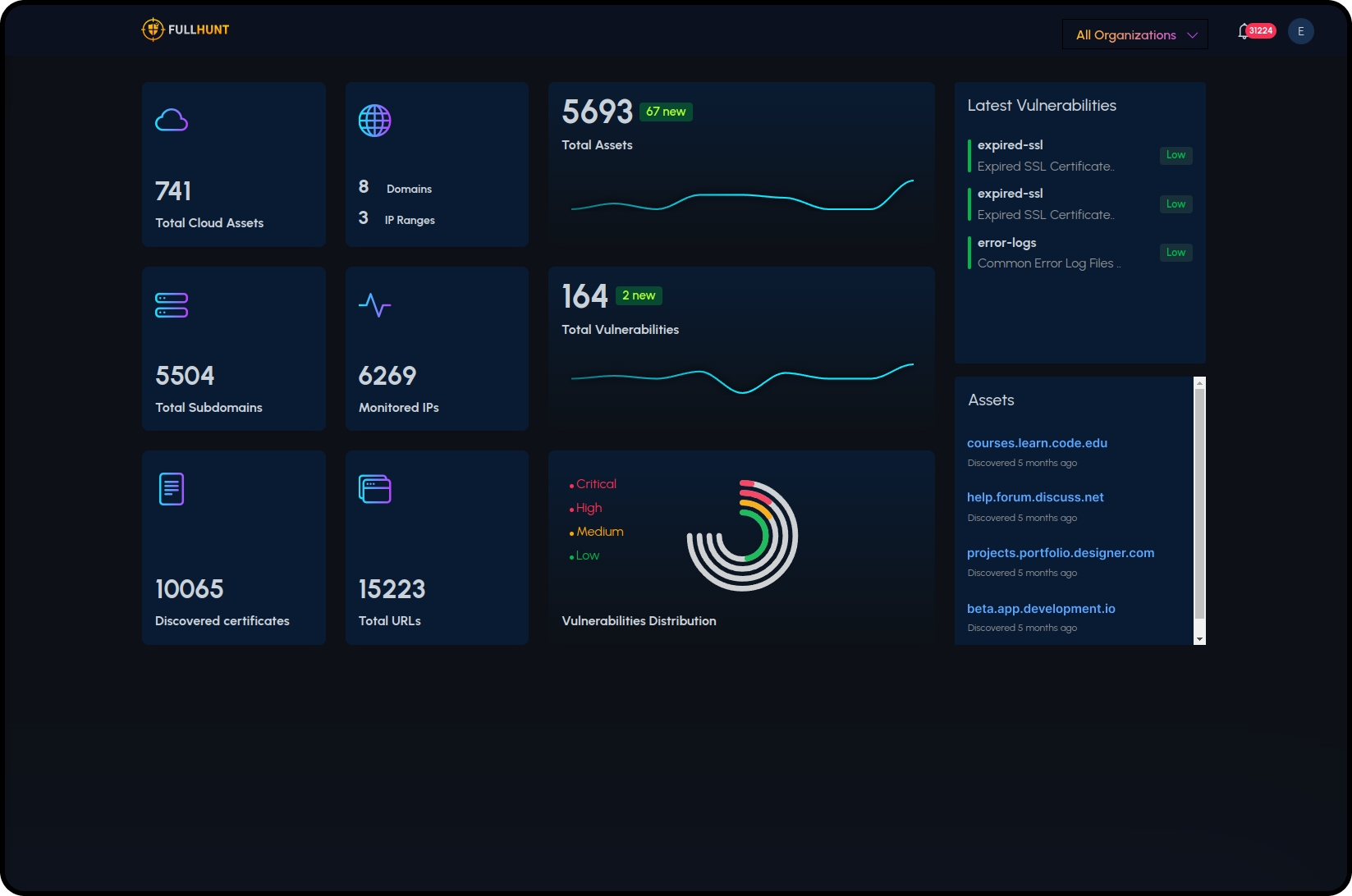

Large Attack Surface Database
FullHunt maintains one of the largest attack surface
database
of the entire Internet.


Comprehensive Suite
Offers a suite of External Attack Surface Management products and services to cover a wide range of use cases.
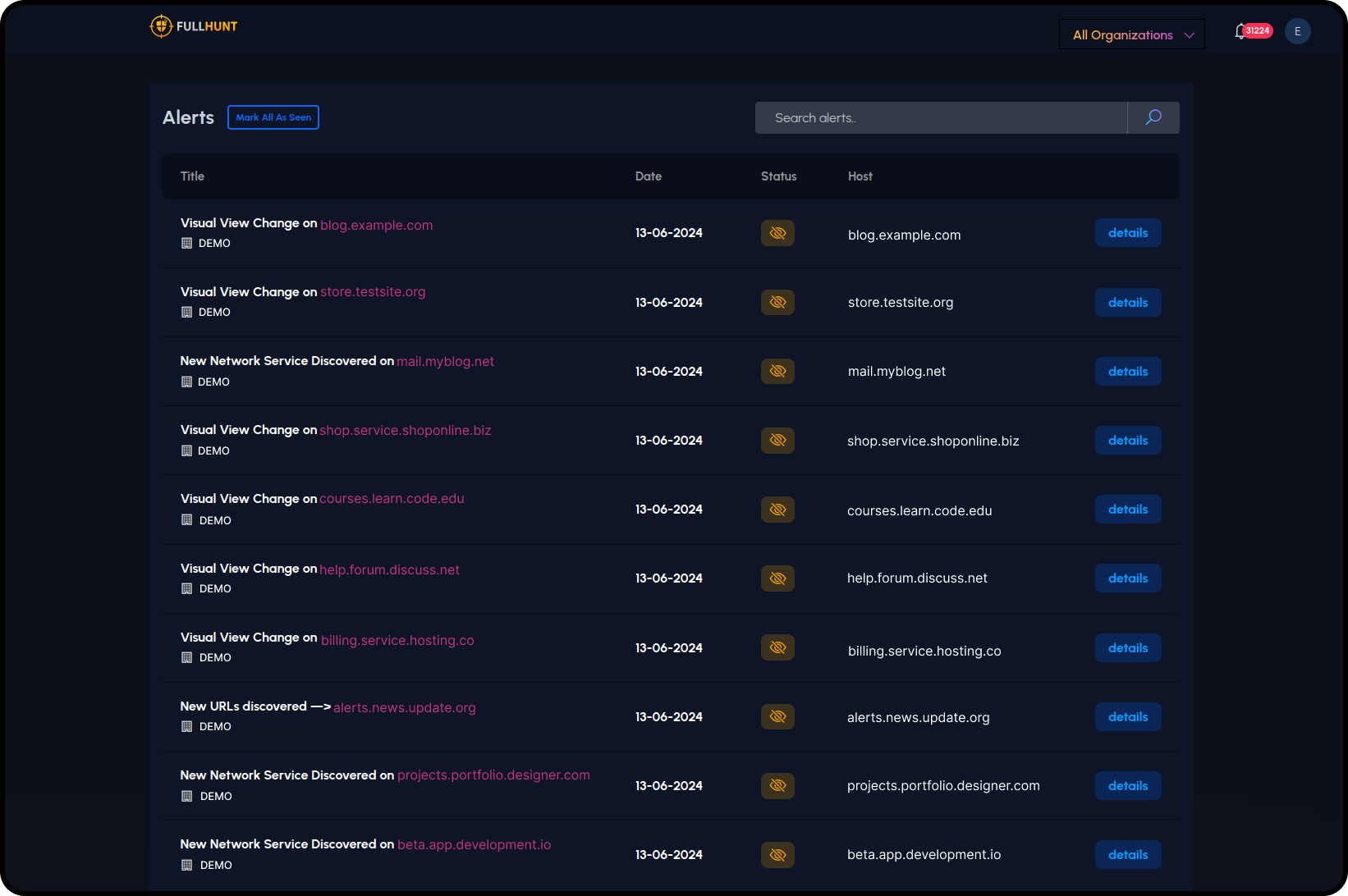

Zero Configuration
FullHunt automatically discovers your external attack surface, no configuration is needed.
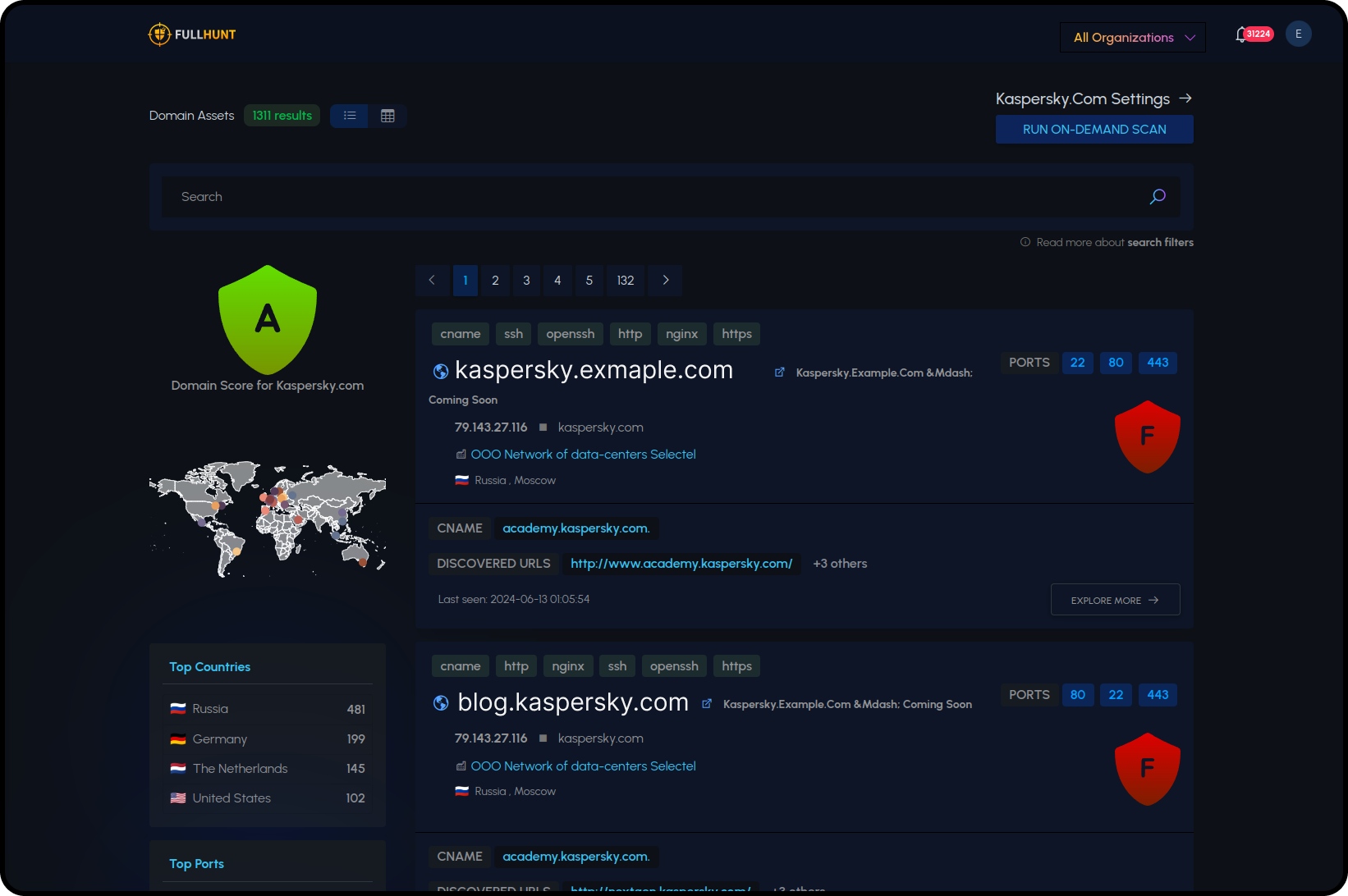

How FullHunt Works?
A comprehensive platform designed to solve Attack Surface Management risks at scale. Here is how it works:
Discover
FullHunt cloud-distributed engines discover and map your entire external attack surface in minutes.
Monitor
FullHunt Assets Monitor continuously profiles and identifies changes and exposures of your assets.
Detect
FullHunt Eagle automatically scans your external assets for security vulnerabilities, evaluating risks, and pinpointing security misconfigurations.
Alert
FullHunt Enterprise Engine sends Real-Time Alerts whenever a risk or exposure is identified.
Our Features
World-Class features for the best security teams in the world.
Asset Discovery
Within seconds, discover all your external assets, shadow-IT assets that you didn’t know about.
AI-Powered Capabilities
FullHunt engines are AI-powered to deliver advanced offensive security capabilities and data.
Real-Time Notification
Be notified whenever a change happens to your public infrastructure.
Assets Inventory and Database
Use FullHunt as your automated assets inventory and database for your external attack surface. No human interaction is required.
DarkWeb Monitoring
Run continuous scans on the dark web and be alerted for dark web risks in your organization.
Penetration-Test-As-Service
FullHunt conducts world-class penetration test engagements by experts and security engineers.
Third-Party Risk Management
FullHunt has Third Party Management capabilities to identify third-party risks and vulnerabilities through the FullHunt Asset Score framework.
Automated Vulnerability Validation
FullHunt uses proprietary technologies to validate whenever vulnerabilities are fixed and remediated and automatically informs organizations about the vulnerabilities' remediation.
Continuous Vulnerability Scanning
FullHunt performs continuous security scanning of all your assets and reports to you whenever a vulnerability is identified across all your assets. Everything is 100% automated.

The First-Ever Assets Monitoring Technology
FullHunt built the first enterprise-level framework for monitoring the External Attack Surface for changes and exposure. The framework has been evolving over the years to provide accurate intelligence to organizations worldwide.
Solving Attack Surface Management, at scale.

The Start
FullHunt started as a project to solve a security challenge that all companies face today: Understanding the current exposure and performing continuous monitoring.
The Growth
FullHunt grew from a community project to become one of the leading Attack Surface Management in the market.

The Expand
FullHunt now provides a suite of products to help build and mature your security program, including Continuous Attack Surface Management, DarkWeb Monitoring, Third Party Risk Management, Data Intelligence APIs, Global Internet Space Scanning, and Penetration-Test-As-A-Service. Everything is powered by the FullHunt technology.

FullHunt Integrates With All Workflows And Playbooks
FullHunt provides a comprehensive set of APIs and integrations to help you automate your security workflows and playbooks.
Use some of the following integrations natively within the FullHunt Platform
Modern Continuous Security at scale

FullHunt Community Platform
Basic Discovery is used by Security researchers and professionals for initial discovery. Free for everyone, forever.
Get Started
FullHunt Enterprise Platform
The Complete Attack Surface Management Platform. Used by Security teams for Continuous Discovery, Monitoring, and Vulnerability Scanning at scale.
Get Started






