Enterprise External Attack Surface Management
Continuous discovery, change monitoring, runtime-validated vulnerabilities, and dark web monitoring; without the false-positive noise.
What the Platform Does
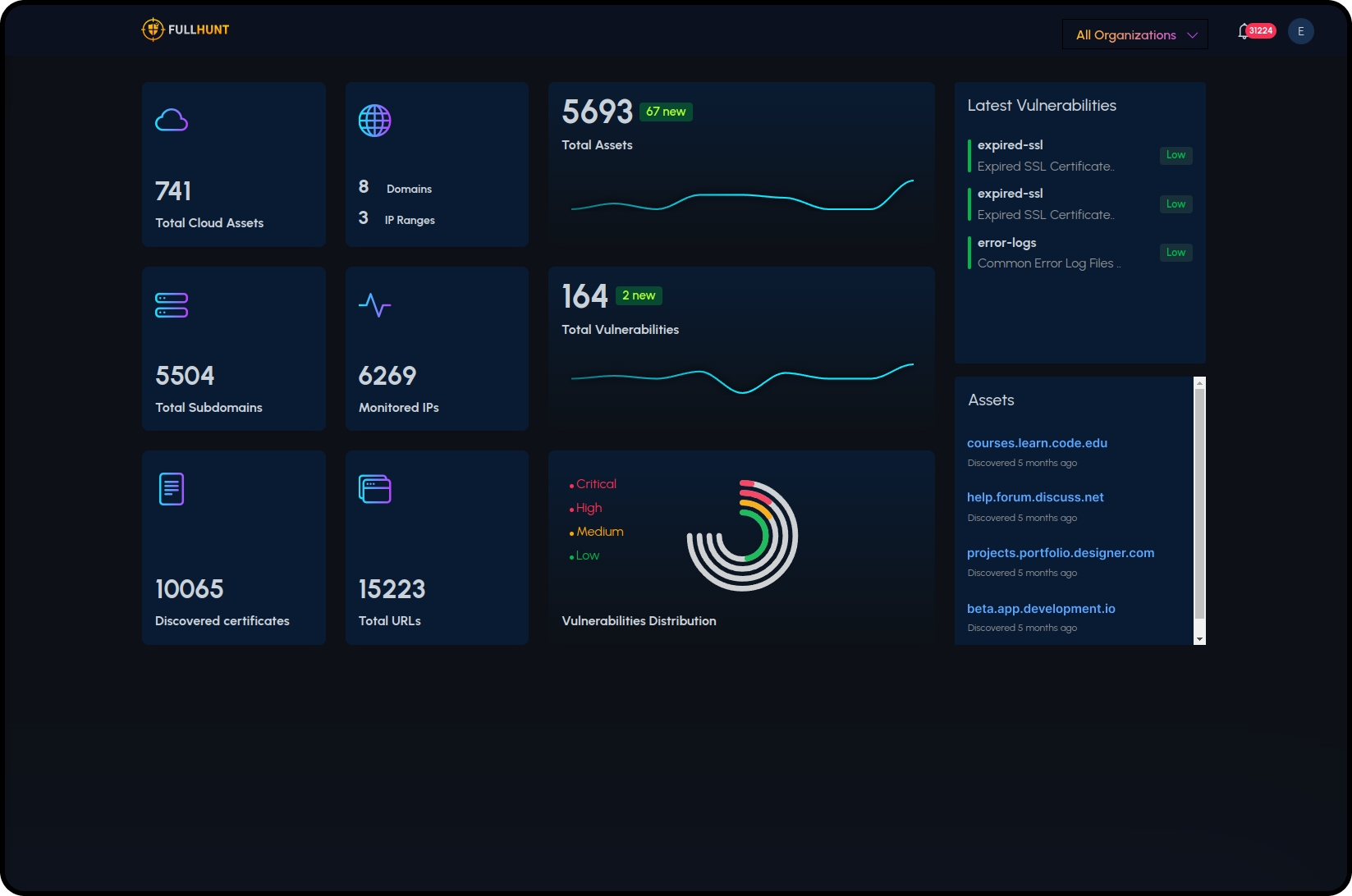
The Enterprise ASM platform discovers your complete external footprint and keeps it current. It fingerprints technologies, attributes assets to the right business units, and tracks change over time. High-fidelity checks validate misconfigurations and vulnerabilities continuously, so teams can focus on exploited and exploitable risk.
Continuous Asset Discovery
Map domains, subdomains, IPs, cloud services, and technology stacks continuously. FullHunt discovers shadow IT automatically, without agents or network access.
- Automated subdomain enumeration
- Cloud asset discovery (AWS, Azure, GCP, Alibaba Cloud, Oracle Cloud)
- Technology fingerprinting (thousands of signatures)
- Organization attribution
- Certificate tracking

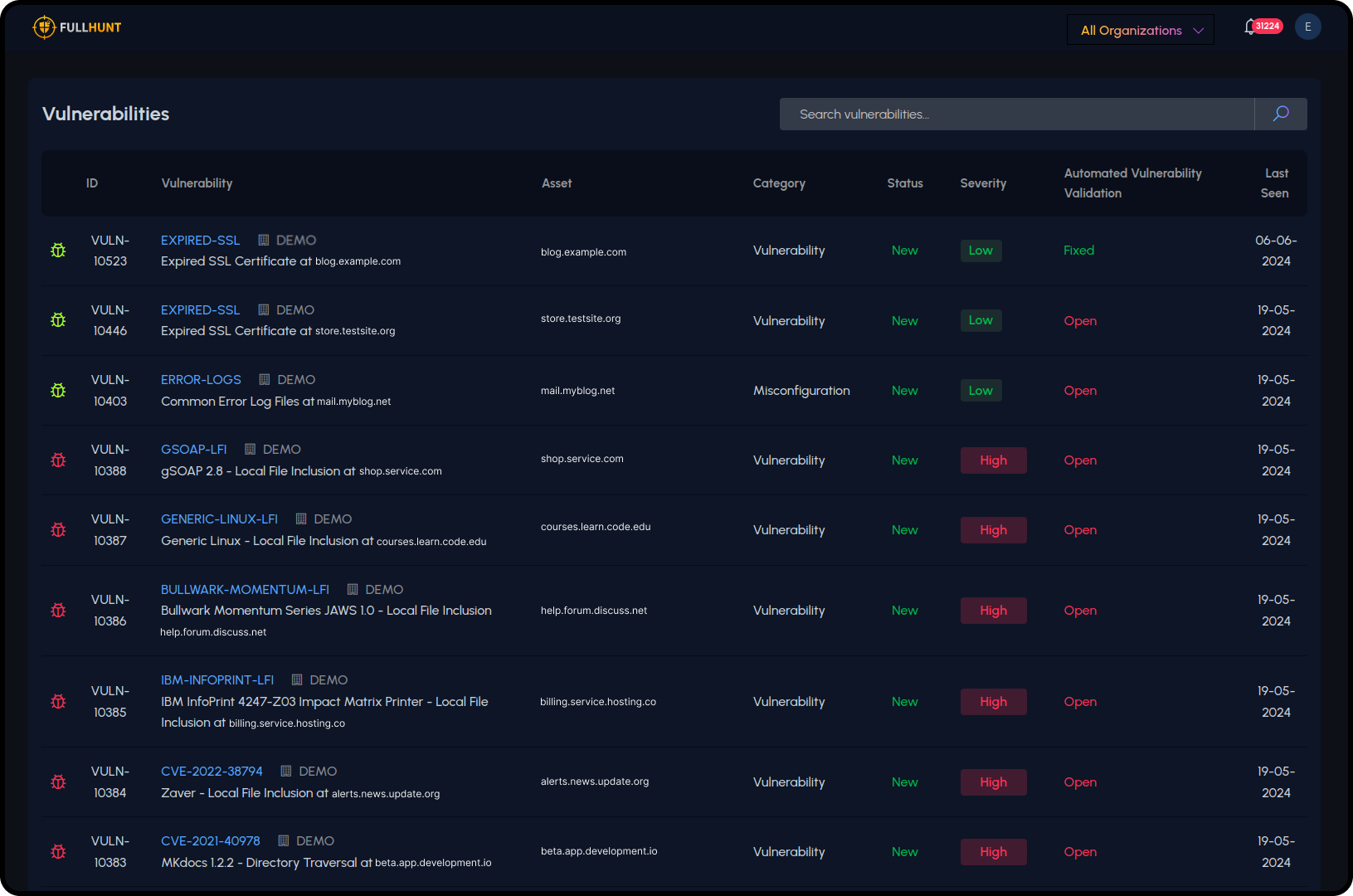
Runtime-Validated Vulnerabilities
High-fidelity validation with thousands of security checks. Every vulnerability is verified to ensure zero false positives.
- Thousands of vulnerability checks
- Runtime validation for accuracy
- EPSS & KEV enrichment
- Public exploit correlation
- Asset scoring based on exploitability
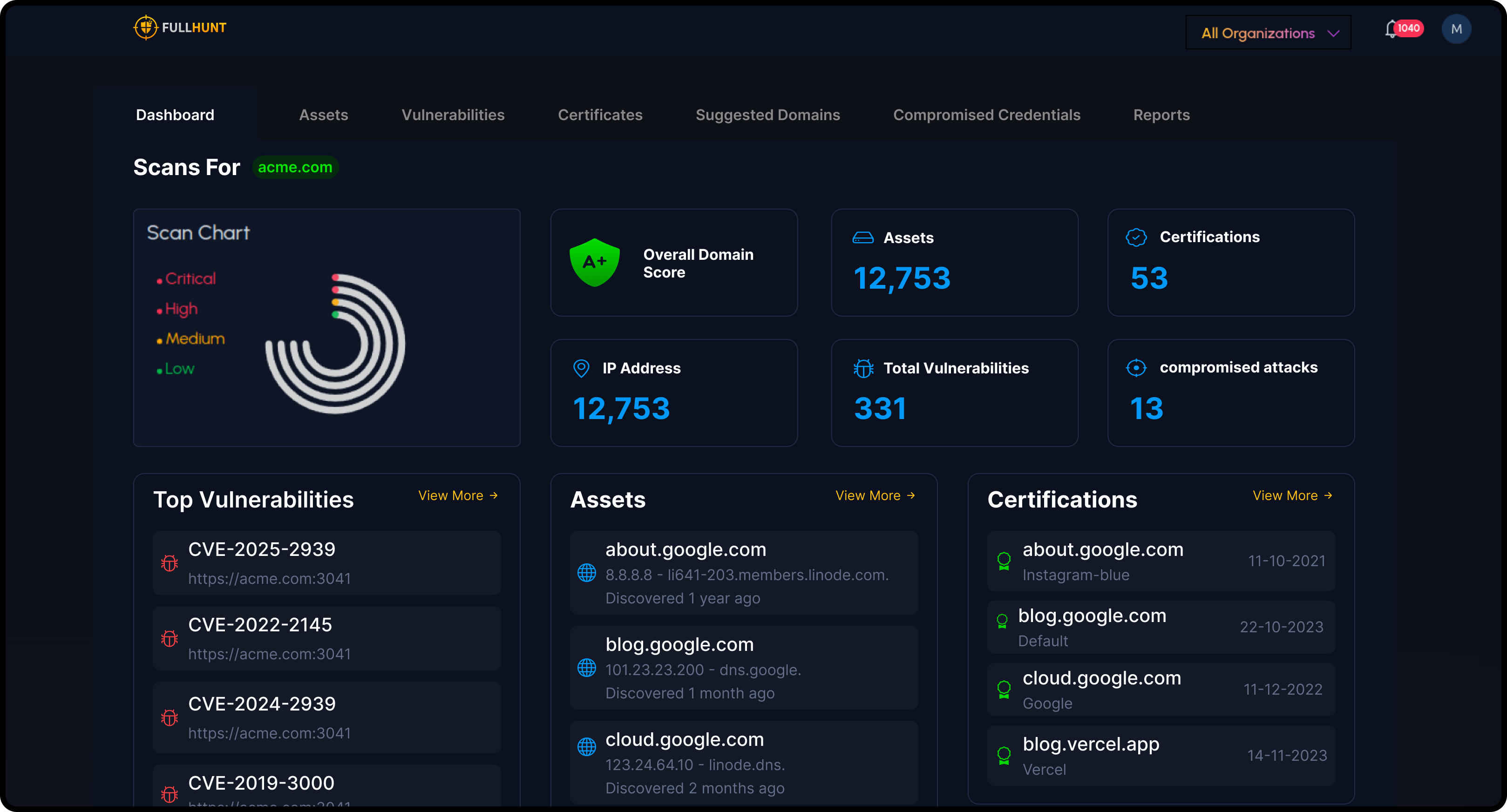
Intelligent Prioritization
Focus on what matters with exploit-aware prioritization. FullHunt enriches findings with real-time intelligence to help teams tackle critical issues first.
- CISA KEV tracking
- EPSS probability scoring
- Real-time exploit correlation
- Curated security research
- Risk-based prioritization
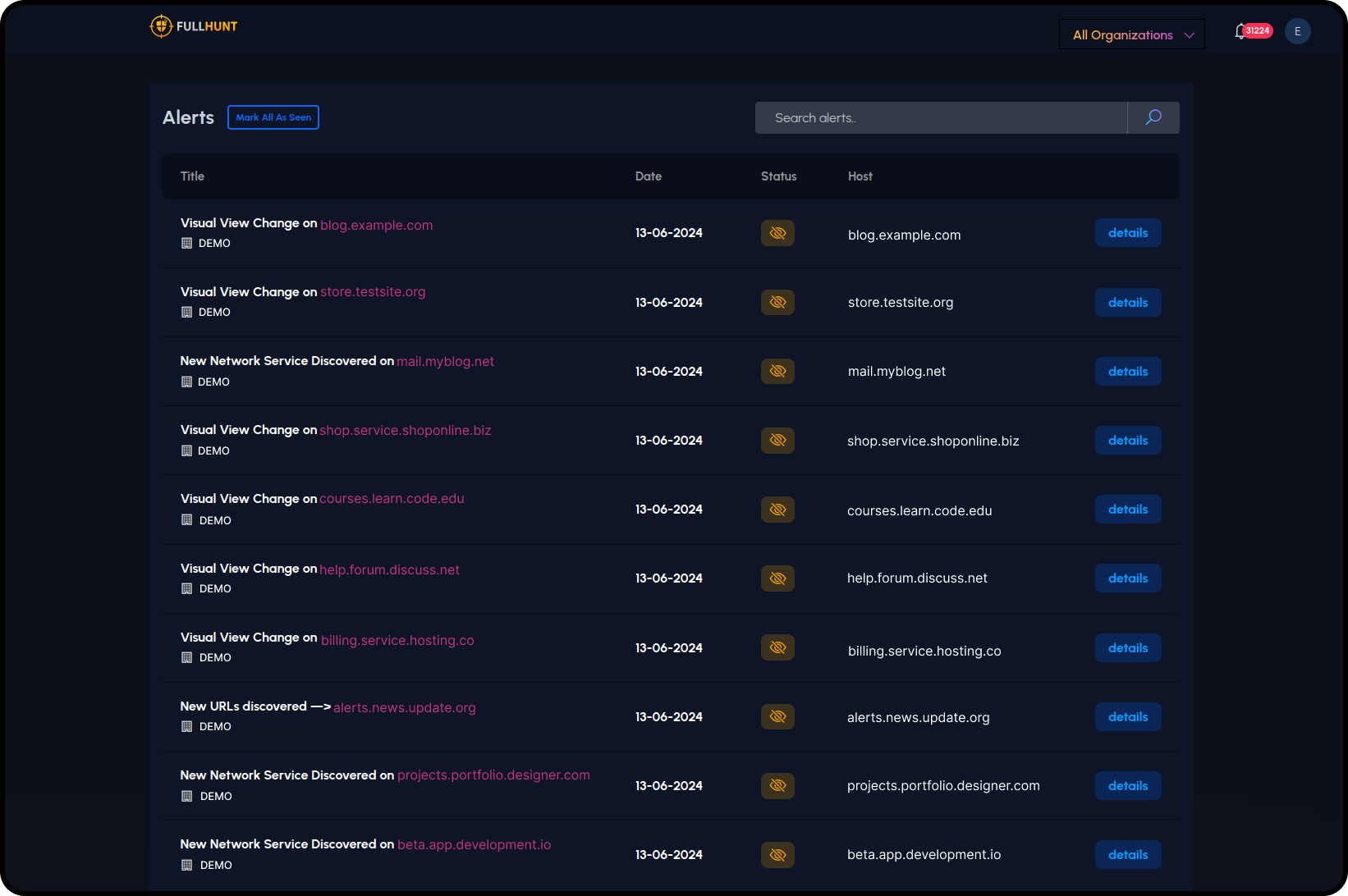
Automated Alerts & Integrations
Route findings directly into your existing workflows. Native integrations push alerts to SIEM, SOAR, and ticketing systems automatically.
- SIEM/SOAR integrations (Splunk, XSOAR, FortiSOAR)
- Ticketing systems (Jira, ServiceNow)
- Chat & collaboration (Slack, Teams)
- Webhooks & REST APIs
- Exportable reports (CSV, JSON, PDF)
Key Outcomes
Shrink the Attack Surface
Decommission forgotten assets and close exposures faster with complete visibility.
Prioritize What Matters
Use exploit context and asset criticality to focus on real risk, not noise.
Accelerate Remediation
Route issues automatically to your workflows with native integrations.
Whether you're preparing for audits, standardizing remediation SLAs, or building a continuous exposure management program, FullHunt turns unknowns into a manageable queue.
Complete Capability Set

Continuous Asset Discovery
Map domains, subdomains, IPs, cloud services, and tech stacks continuously.

Change Monitoring
Track exposures, new services, and misconfigurations in real time.

Runtime-Validated Checks
High-fidelity validation for thousands of issues with automated scanning.

Vulnerability Prioritization
EPSS scoring, KEV tracking, and exploit correlation for risk-based prioritization.

Dark Web Monitoring
Typosquatting, phishing lookalikes, compromised credentials, and leaks.

Third-Party Risk
Extend coverage to vendors and subsidiaries with automated asset scoring.
Native Integrations
SIEM, SOAR, ticketing systems, and webhooks for automated workflows.

Comprehensive Database
Automated inventory of all external assets with up-to-date records.
Executive Reporting
Exportable reports with dashboards for CISOs and security engineers.
Why Teams Choose Enterprise ASM
Continuous, Not Point-in-Time
Unlike periodic scans, FullHunt runs continuously. Catch changes as they happen with no blind spots between assessments.
High Signal, Low Noise
Runtime validation cuts false positives dramatically. Your team works on real issues, not chasing ghosts.
Built to Integrate
Findings go where your team already works. No manual exports or context switching required.
Fast Time to Value
Get operational in under 30 minutes. See your entire external footprint in seconds, not days.
Ready to secure your attack surface?
See how FullHunt Enterprise ASM can transform your security posture.