OEM Attack Surface & Intelligence APIs
White-label FullHunt's attack surface discovery and vulnerability intelligence into your security platform. Embed internet-scale capabilities without building scanning infrastructure.

Ship Security Features Faster
Build features customers want without building scanning infrastructure. With OEM APIs, security vendors can embed discovery, monitoring, and vulnerability intelligence directly into their platforms. Deliver search, asset inventory, exposure insights, and exploit-aware prioritization under your brand. Launch in weeks, not years, with full white-label support.
Complete White-Label Integration
Embed FullHunt's capabilities seamlessly into your product. Your customers see your brand, your UI, and your value proposition powered by FullHunt's infrastructure.
- Custom branding and domain names
- Your logo and product identity
- Flexible API response formatting
- White-label documentation options
- Seamless customer experience
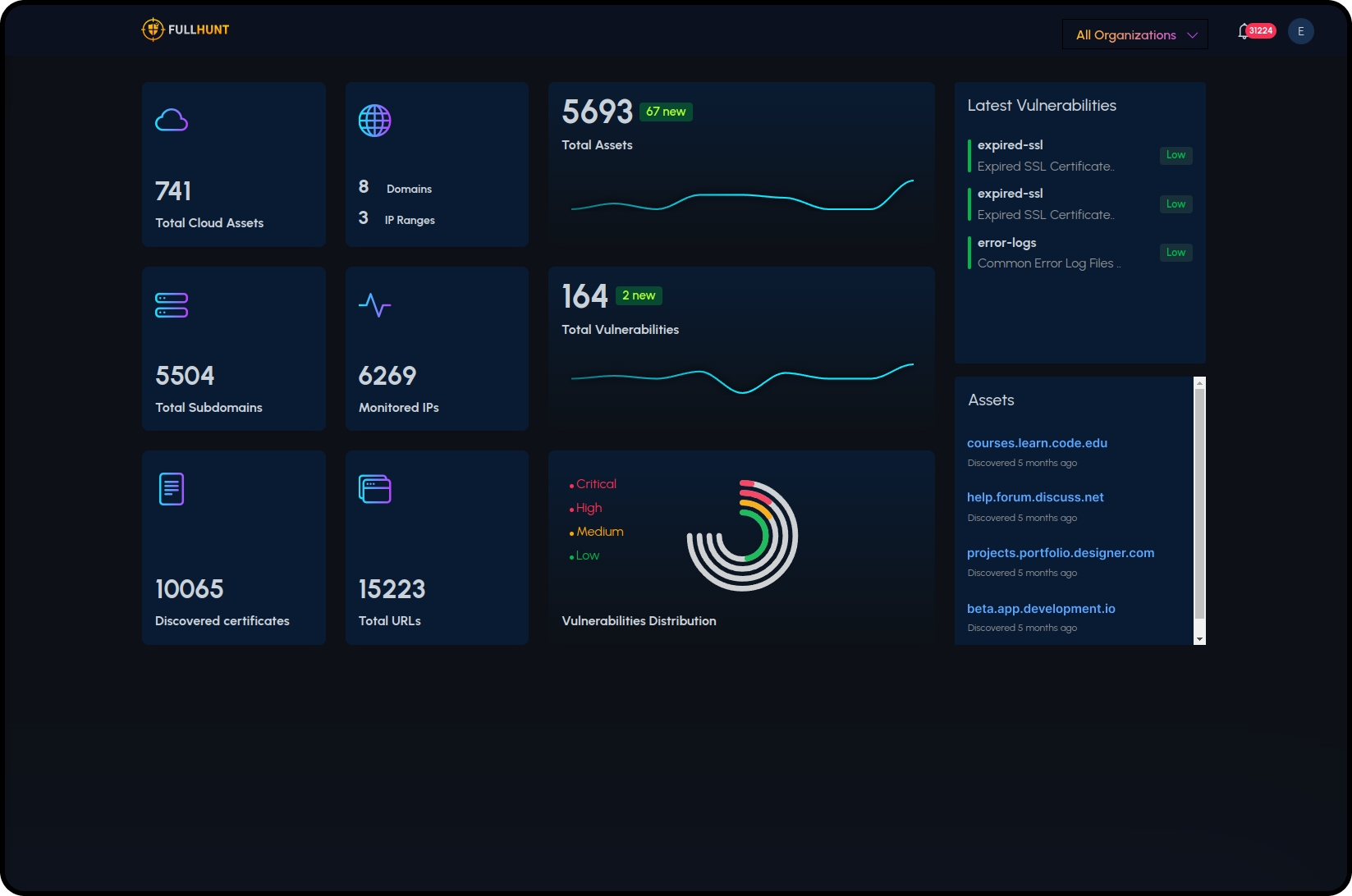
Complete Feature Set
Access all FullHunt capabilities through comprehensive APIs. From discovery to vulnerability intelligence, your platform gets the full stack.
- Attack surface discovery and mapping
- Continuous monitoring and change detection
- Vulnerability scanning and validation
- EPSS, KEV, and exploit intelligence
- Real-time threat intelligence feeds
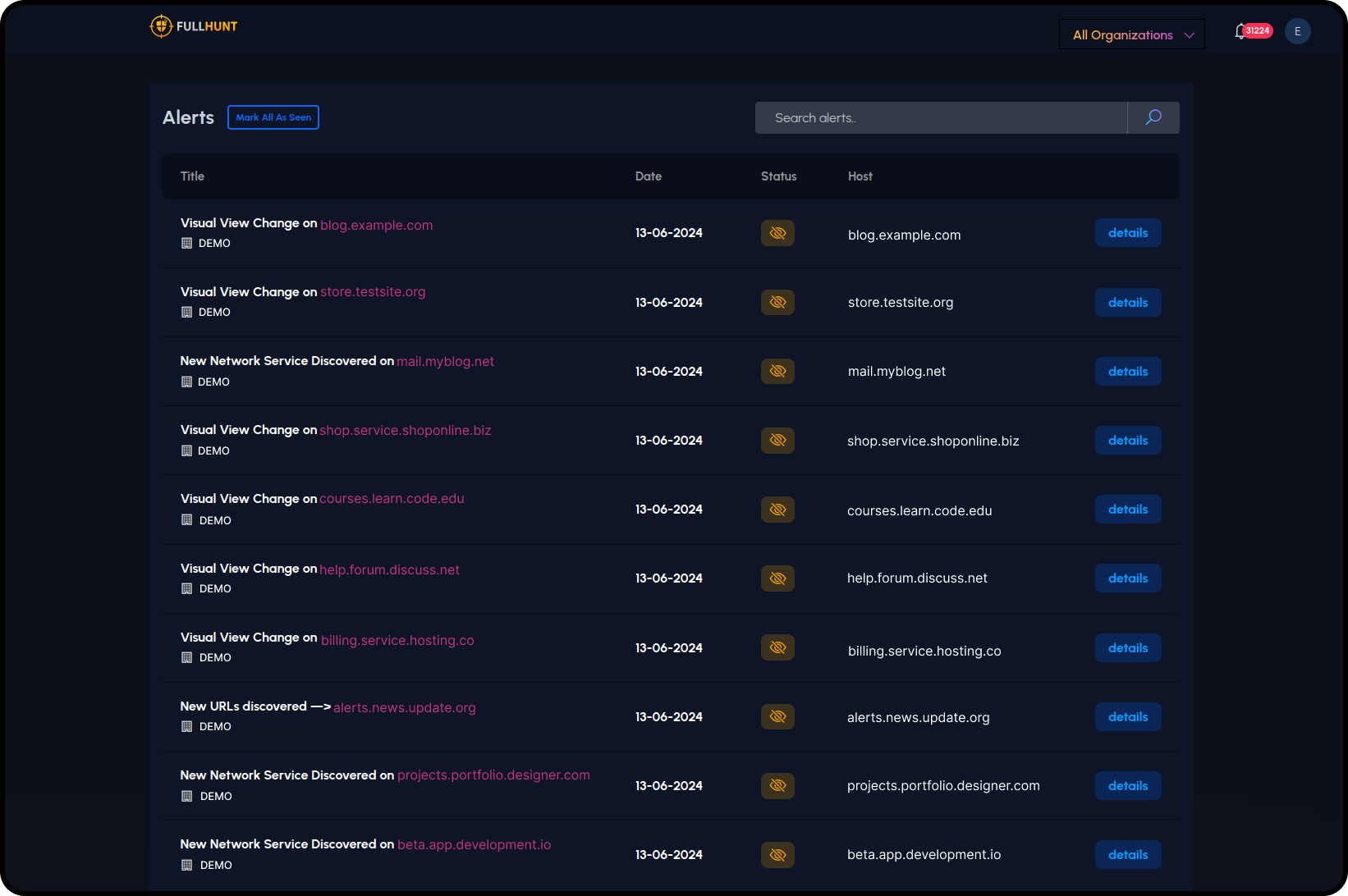
Flexible Licensing Models
Choose licensing that fits your business model. Revenue sharing, volume discounts, and custom arrangements available.
- Reseller and distributor programs
- Revenue sharing agreements
- Volume-based pricing tiers
- Custom commercial terms
- Flexible billing options

Dedicated Partner Support
Get technical integration help, co-marketing opportunities, and dedicated account management to ensure your success.
- Dedicated technical account manager
- Integration engineering support
- Co-marketing and joint campaigns
- Partner enablement and training
- Priority API support
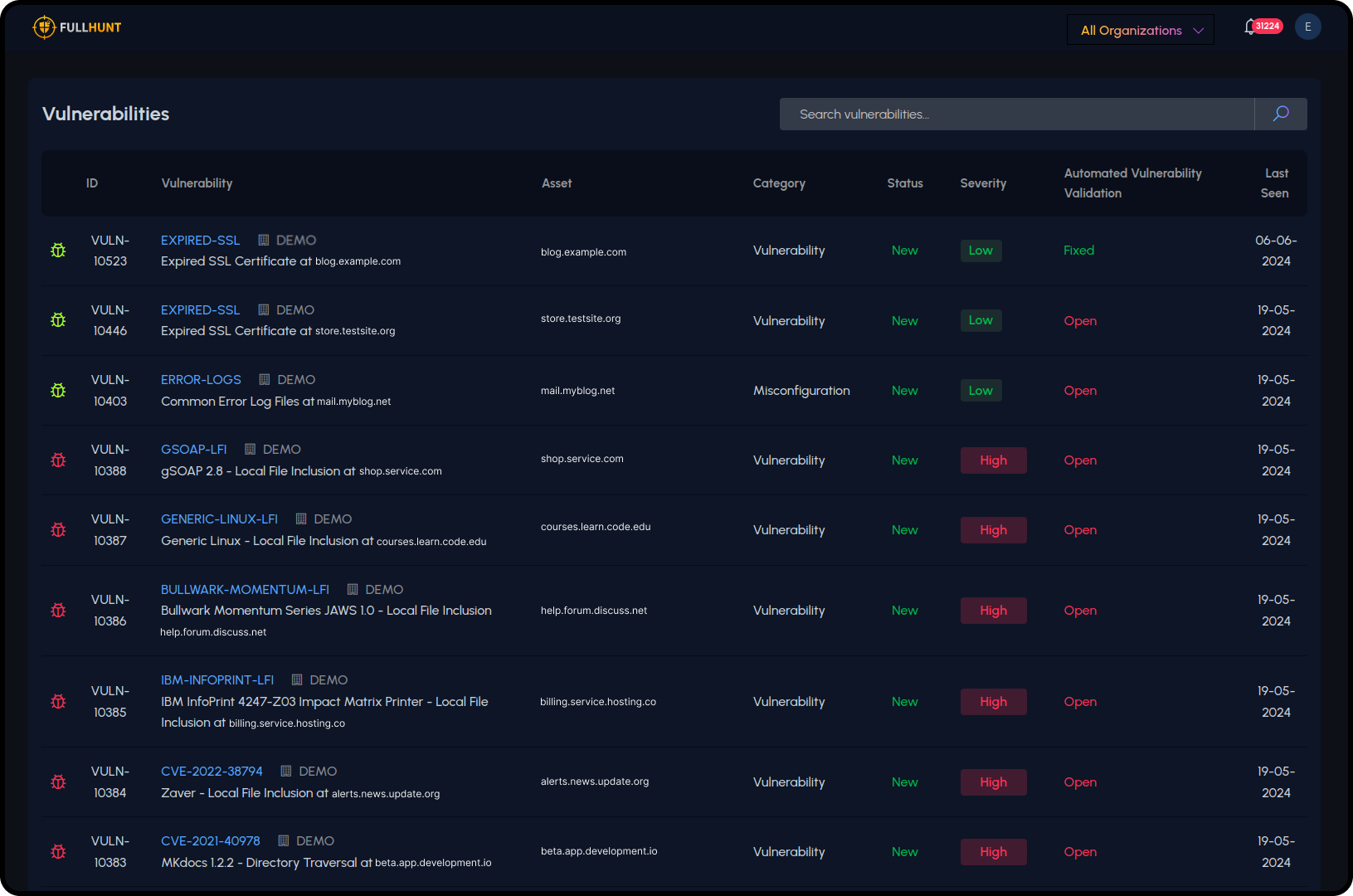
Ideal For These Platforms
Security Vendors
Embed attack surface management into vulnerability management or GRC platforms.
MSSP Platforms
Add attack surface monitoring as a managed service offering for clients.
Risk Management Tools
Enhance vendor risk and third-party risk management platforms with external scanning.
Compliance Platforms
Add external attack surface visibility to compliance and audit management tools.
Threat Intelligence
Enrich threat intelligence platforms with attack surface context and exposure data.
Security Dashboards
Add external asset inventory and vulnerability tracking to security dashboards.
Partner Benefits
Faster Time-to-Market
Launch attack surface features in weeks instead of years. Skip building infrastructure and focus on your product differentiation.
Complete White-Label
Deliver under your brand with customizable responses, flexible licensing, and your customer experience throughout.
Scalable Infrastructure
Enterprise-grade infrastructure scales with your customer base. No performance degradation as you grow.
Dedicated Support
Technical account manager, integration engineering, co-marketing opportunities, and priority API support.
What You Can Embed
Asset Discovery
Internet-scale discovery of domains, subdomains, IPs, and cloud services for your customers.
Exposure Monitoring
Continuous tracking of configuration changes, new services, and security exposures.
Vulnerability Intelligence
EPSS scoring, KEV tracking, and real-time exploit correlation for prioritization.
Technology Fingerprinting
Thousands of product and web technology signatures for comprehensive profiling.
Dark Web Monitoring
Typosquatting, phishing, compromised credentials, and leak detection capabilities.
Third-Party Risk
Vendor and subsidiary assessment capabilities for TPRM features.
Trusted by Leading Platforms
See FullHunt OEM capabilities in action through our marketplace partners




Why Partner with FullHunt
Proven Technology
Battle-tested infrastructure trusted by enterprises and government agencies worldwide for critical security operations.
Continuous Innovation
Platform evolves continuously. Your product gets new capabilities, signatures, and threat intelligence automatically.
Competitive Differentiation
Add capabilities competitors would take years to build. Differentiate with internet-scale visibility and validated intelligence.
Market Leadership
Position your platform as a leader with capabilities that would take competitors years to build and maintain.
Ready to embed attack surface intelligence?
Contact our partner team to discuss OEM capabilities, licensing options, and technical integration.