
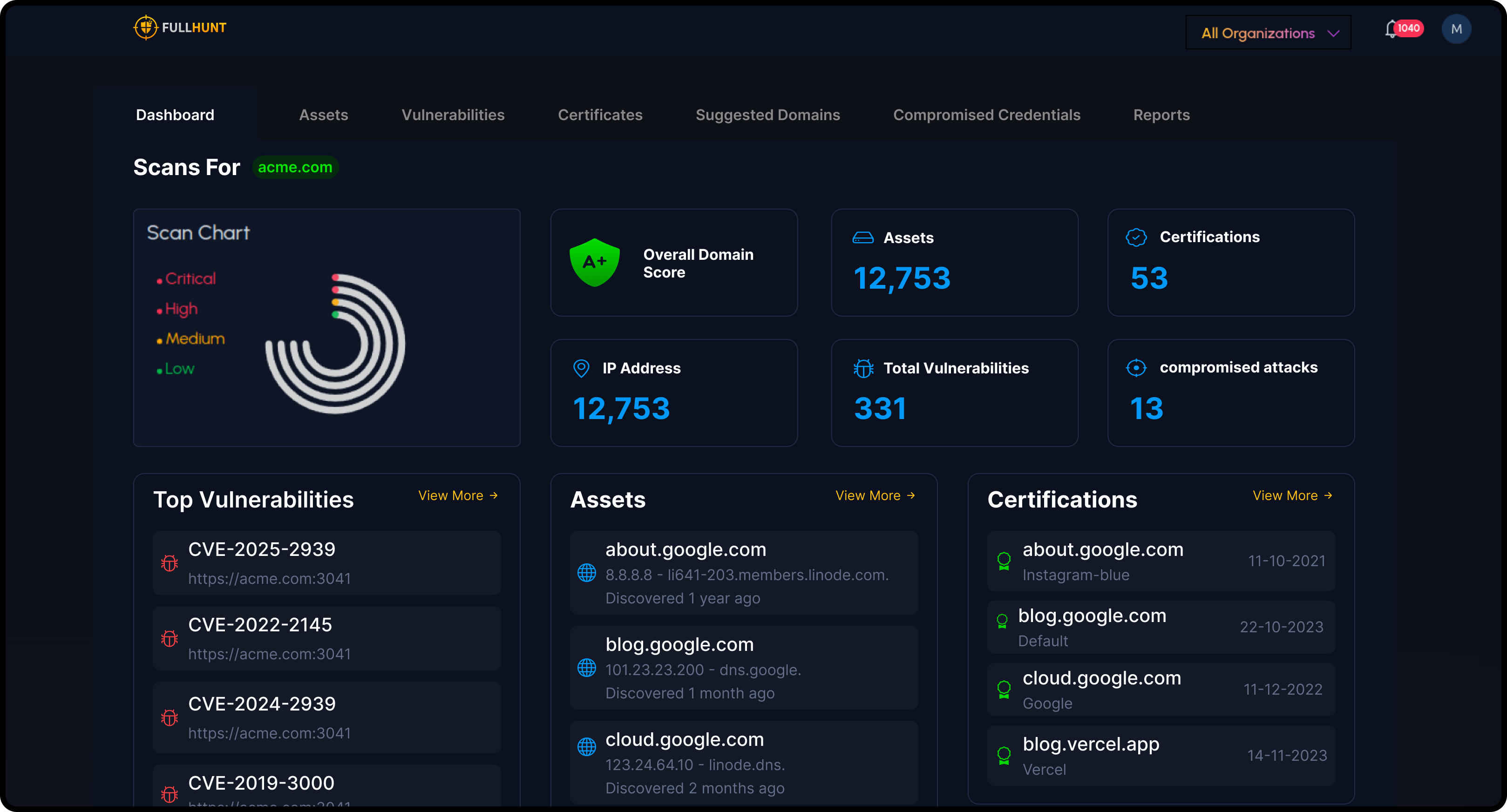
FullHunt Owl
Automated discovery and high-signal vulnerability scanning for subsidiaries, vendors, and one-time assessments. Agentless, fast, and accurate.
What FullHunt Owl Does
When you need immediate clarity on a specific scope (an acquired company, a partner's infrastructure, or a vendor's external assets), Owl delivers fast results. Provide a seed domain or IP range, and Owl automatically discovers related assets, runs high-signal security checks, and packages results into a clean, actionable report. Perfect for spot checks without building new infrastructure.
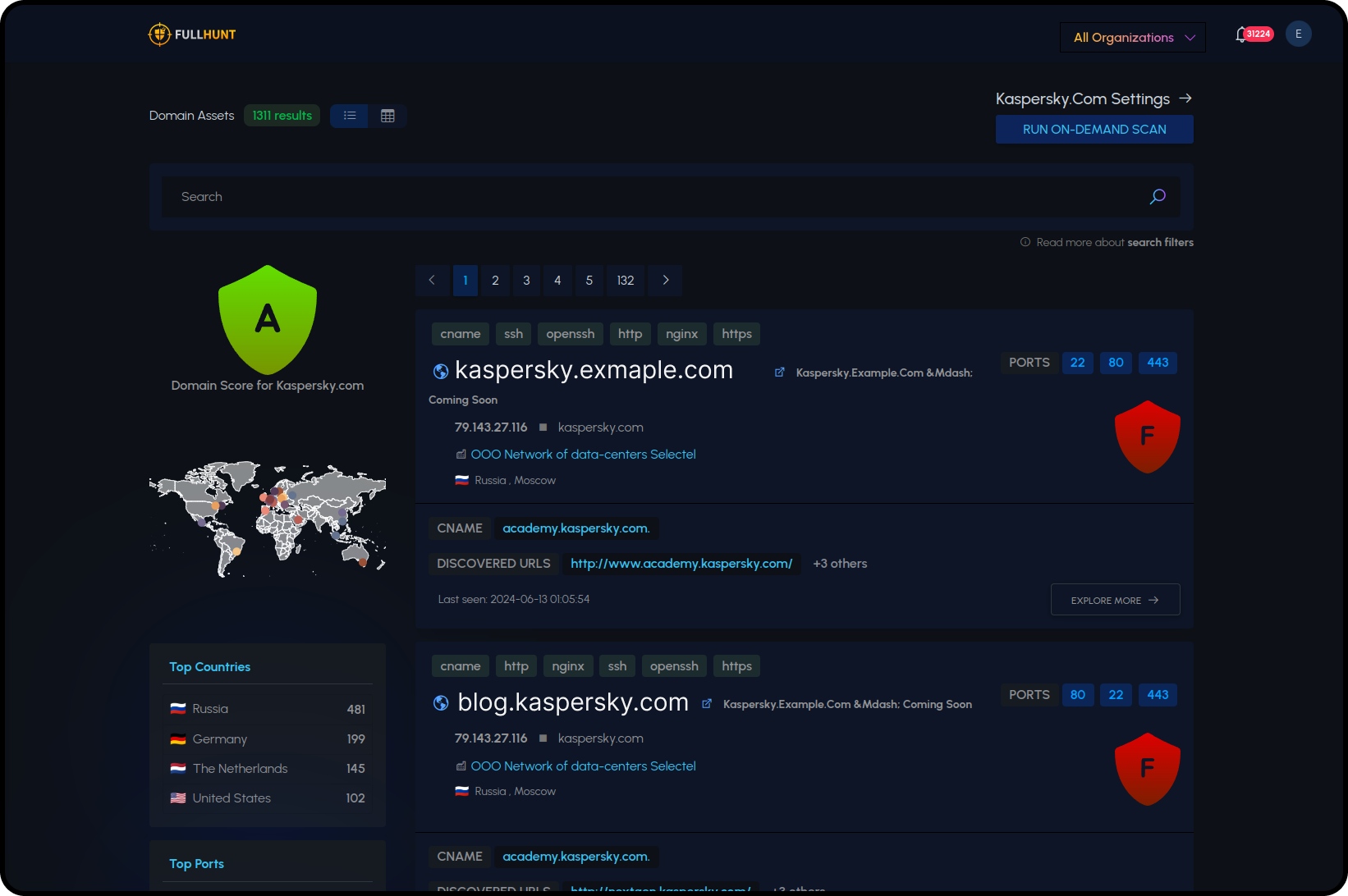
Zero-Touch Discovery
Owl automatically maps the entire external attack surface from a simple seed input. No agents, no network access, no complex setup required.
- Automated subdomain enumeration
- Cloud asset discovery (AWS, Azure, GCP, Alibaba Cloud, Oracle Cloud)
- Technology fingerprinting
- Shadow IT detection
- Complete asset inventory in minutes

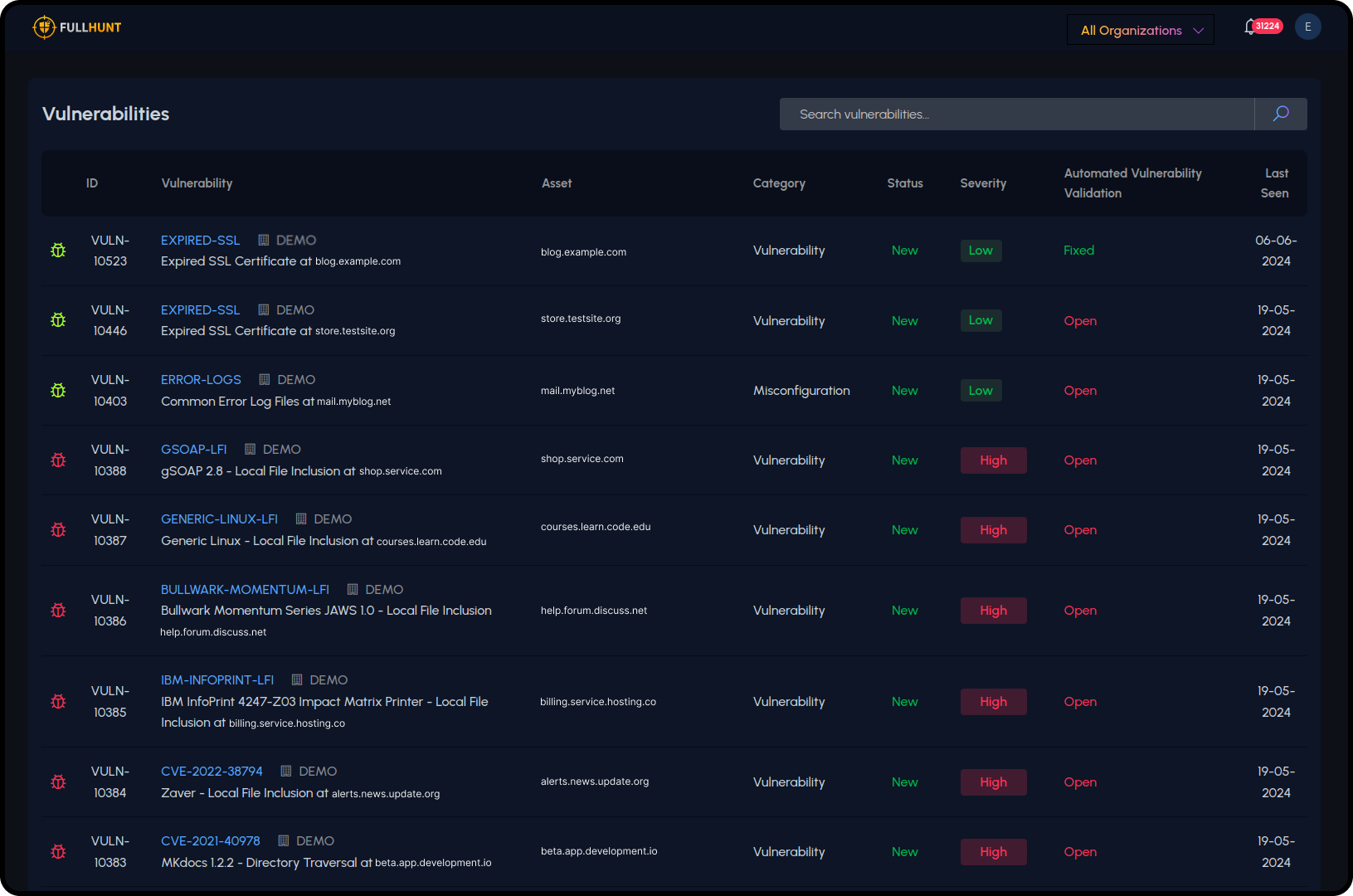
High-Signal Vulnerability Scanning
Validated security checks with low false-positive rates. Owl focuses on exploitable vulnerabilities, not noisy alerts.
- Thousands of automated security checks
- Runtime validation for accuracy
- Prioritized findings by severity
- EPSS and KEV enrichment
- Exploit correlation for critical issues
Rapid Results & Reporting
Get comprehensive scan results in minutes, not days. Executive-ready reports with clear findings and remediation guidance.
- Results delivered in minutes
- Automated executive summaries
- Detailed technical findings
- Remediation recommendations
- Exportable reports (PDF, CSV, JSON)

Flexible Deployment Models
Use Owl for one-time scans, recurring assessments, or continuous monitoring. Scale from single scopes to thousands of targets.
- One-time security assessments
- Recurring vendor scans
- Subsidiary monitoring
- M&A due diligence
- API-driven automation
Ideal Use Cases
MSSPs
Standardize security assessments across clients with consistent methodology and professional reporting.
M&A Due Diligence
Rapidly assess acquisition targets' external security posture before deals close.
Vendor Assessments
Evaluate third-party vendor security without requiring internal access or lengthy questionnaires.
Subsidiary Security
Discover and continuously monitor security across subsidiary companies and business units.
How FullHunt Owl Works
Provide Scope
Enter a domain, IP range, or company name to scan.
Automated Discovery
Owl maps all related assets, subdomains, and services automatically.
Security Scanning
Thousands of security checks validate vulnerabilities and misconfigurations.
Get Report
Receive executive-ready reports with findings and remediation guidance.
Key Benefits
Minutes, Not Days
Complete scans in minutes instead of waiting days or weeks. Get immediate insights into external security posture.
No Infrastructure Required
Agentless scanning means no software to install, no credentials needed, and no network changes. Scan from outside-in.
High Accuracy, Low Noise
Validated findings mean teams work on real issues. No wasted time chasing false positives or unverified alerts.
On-Demand Rescanning
Retest anytime to verify remediation or track changes. Automated retests confirm fixes without manual work.
Perfect For These Scenarios
Mergers & Acquisitions
Quickly assess the external security posture of acquisition targets. Discover inherited risks before they become your problems.
- Pre-acquisition security assessment
- Hidden exposure discovery
- Risk quantification for deals
- Post-merger integration planning
MSSP Client Assessments
Deliver consistent, professional security assessments to clients without building custom infrastructure for each engagement.
- Standardized assessment methodology
- White-label reporting options
- Scalable across many clients
- Recurring assessment packages
Third-Party Vendor Risk
Assess vendor security posture externally as part of TPRM programs. No questionnaires needed; see what's actually exposed.
- External vendor security assessment
- Continuous vendor monitoring
- Risk scoring and reporting
- Compliance documentation
Subsidiary Monitoring
Map and monitor security across all subsidiary companies and business units in your organization.
- Multi-entity security visibility
- Consolidated risk reporting
- Shadow IT discovery
- Centralized security oversight
Why Teams Choose FullHunt Owl
Fast Setup
Start scanning in minutes with zero infrastructure or complex configuration.
Accurate Results
High-signal findings with validation to eliminate false positives.
Scalable
Scan one target or thousands; Owl scales to your needs.
Clear Reports
Professional reports ready for executives and technical teams.
Ready to scan on demand?
FullHunt Owl delivers fast, accurate security assessments for any scope, without infrastructure requirements.