Vulnerability Intelligence
Enriched, actionable intel for the CVEs that matter: advanced vulnerability intelligence with curated security research and real-time exploit tracking delivered to your console and APIs.
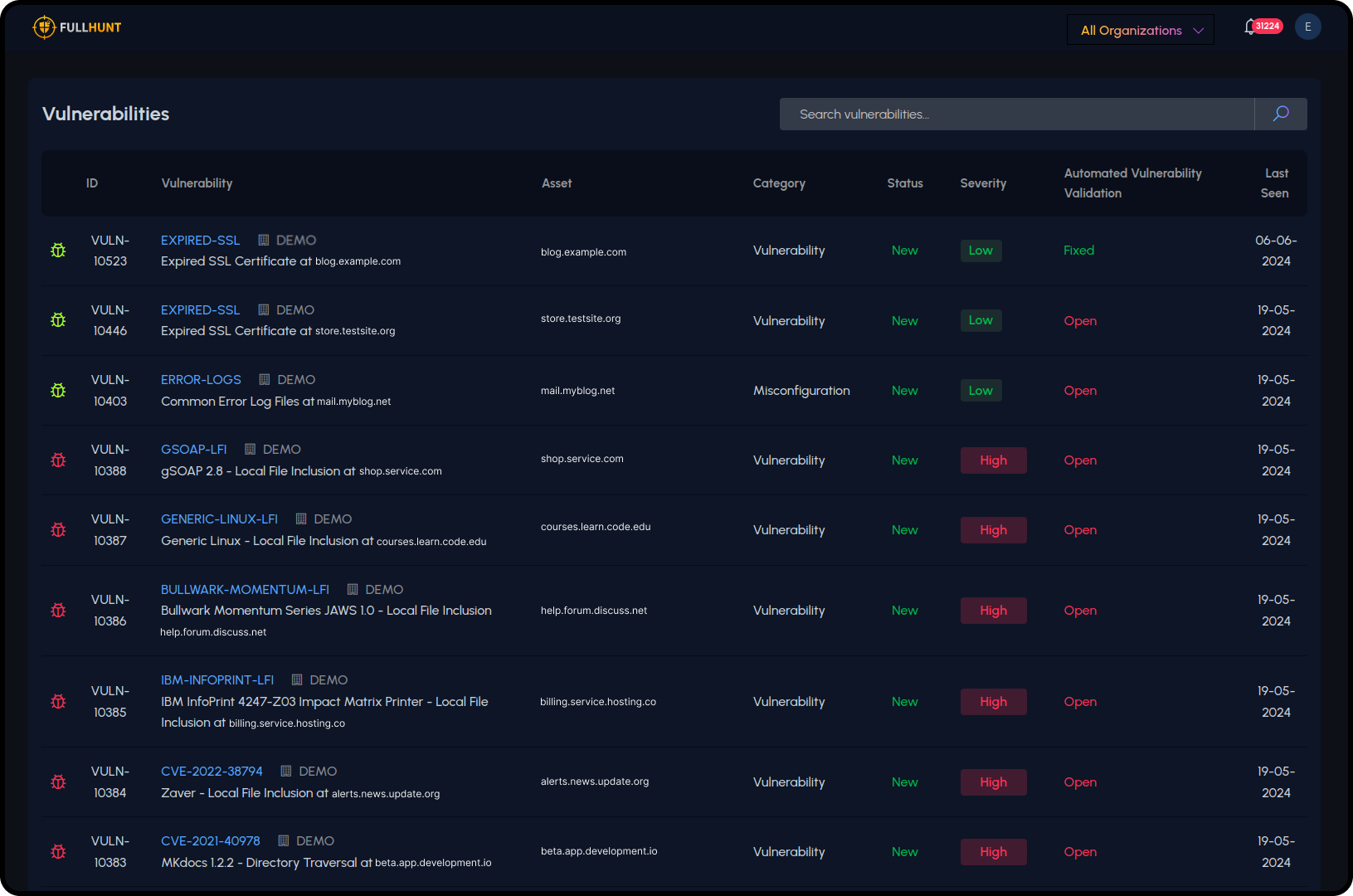
Prioritize What Matters
Vulnerability Intelligence helps teams cut through CVE noise by focusing on what's likely to be exploited. Findings are enriched with advanced vulnerability intelligence, curated security research, and real-time exploit tracking. Within the console, you can pivot from a CVE to affected assets in seconds; via API, you can push the same context into your existing workflows.
Public exploits tracked and indexed in real-time
Exploit Prediction Scoring System integration
CISA Known Exploited Vulnerabilities tracking
EPSS Scoring & Exploit Prediction
Leverage EPSS (Exploit Prediction Scoring System) to understand the probability of exploitation. FullHunt automatically enriches vulnerabilities with EPSS scores, helping you prioritize patches based on likelihood of real-world exploitation.
- Exploit prediction probability scoring
- Risk-based prioritization
- Data-driven remediation decisions
- Automatic EPSS enrichment for all CVEs

KEV Tracking & Active Exploitation
Monitor CISA's Known Exploited Vulnerabilities (KEV) catalog. FullHunt tracks which vulnerabilities are actively being exploited in the wild and flags them for immediate attention.
- CISA KEV catalog integration
- Active exploitation indicators
- Government-verified threats
- Automatic alerts for KEV matches
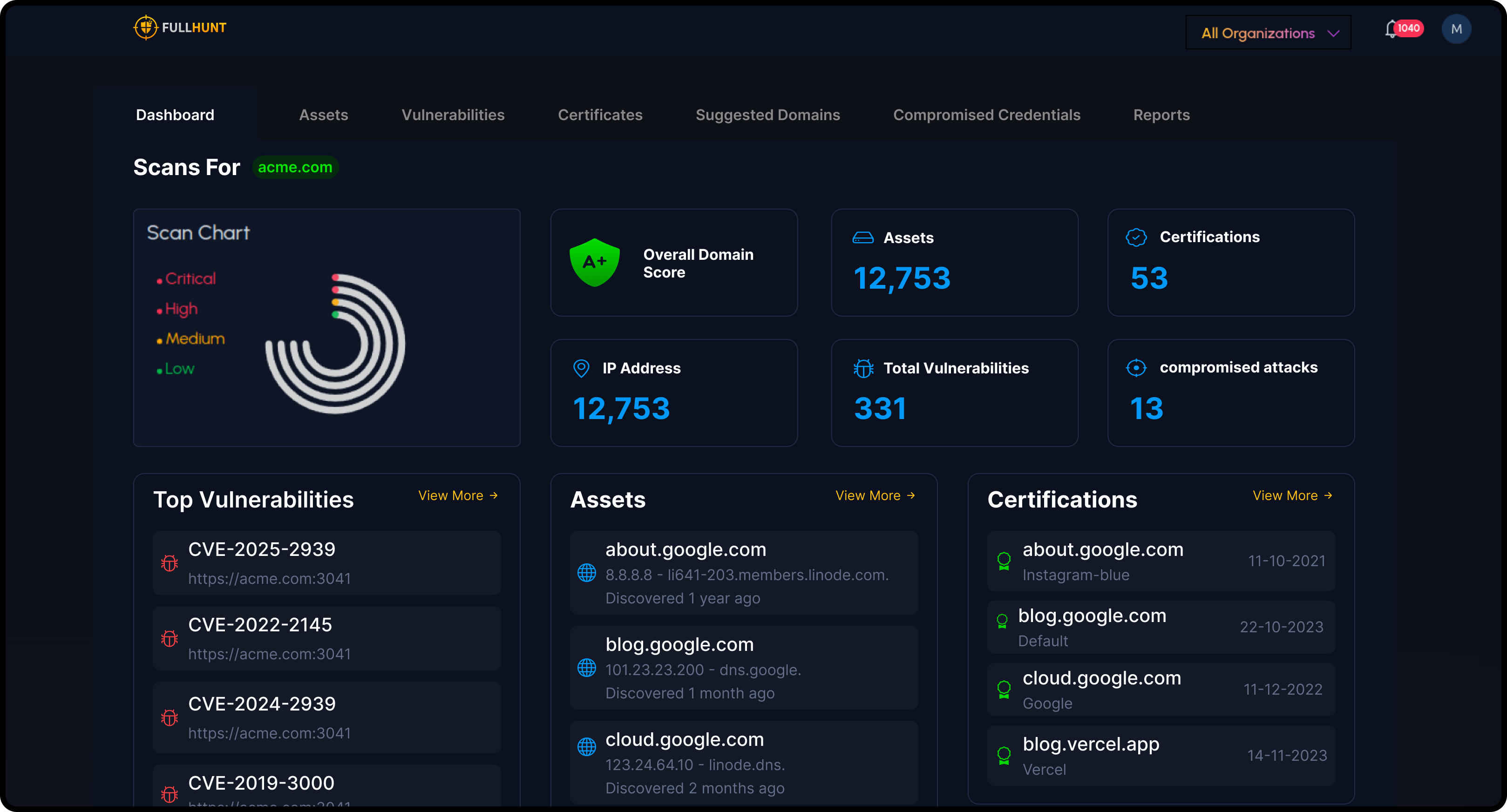
Public Exploit Correlation
Correlate vulnerabilities with publicly available exploits and proof-of-concept code. Know which CVEs have working exploits available to attackers.
- 100,000+ public exploits tracked
- PoC code availability tracking
- Real-world exploitation data
- Exploit maturity indicators

Continuous Enrichment
Vulnerability intelligence updates continuously as new exploits emerge, research papers are published, and threat intelligence feeds refresh.
- Automatic updates as exploits emerge
- Curated security research integration
- Threat intelligence feed correlation
- Real-time enrichment via APIs

How Teams Use It
In Security Operations
Analysts use VI to quickly understand which vulnerabilities need immediate patching. Instead of treating all CVEs equally, teams focus on those with active exploits or high EPSS scores.
Via APIs
Developers pull enrichment data via API to power custom dashboards, automate ticket prioritization, or feed context into SIEM/SOAR platforms for automated playbooks.
For Security Vendors
Security vendors embed VI enrichment to power in-product prioritization features and customer reporting, differentiating their platform with exploit-aware context.
Compliance & Reporting
Generate compliance reports showing which critical vulnerabilities (KEV) have been addressed, with evidence of prioritization logic.
Key Benefits
Smaller Queues
Focus on exploited and exploitable vulnerabilities instead of every CVE. Reduce patch queues by 70%+ with intelligent prioritization.
Faster MTTR
Automated enrichment eliminates manual research. Teams can start remediation immediately with all context at hand.
Fewer Emergency Patches
Catch KEV vulnerabilities early and avoid emergency weekend patch cycles by staying ahead of active exploitation.
Better Metrics
Report on risk reduction using exploit-aware metrics. Show stakeholders you're fixing what matters most.
Intelligence Sources
Public Exploits
100,000+ exploits from GitHub, Exploit-DB, and security research papers
CISA KEV
Government-verified vulnerabilities known to be actively exploited
EPSS Database
ML-driven exploit prediction scores updated daily
Security Research
Curated threat intelligence and security research from the community
Where It Fits in Your Workflow
Use Vulnerability Intelligence alongside your ASM program or feed it into ticketing, SIEM, or SOAR to route critical issues automatically. Security vendors can embed the enrichment to power in-product prioritization and customer reporting. Whether you need a single pane for analysts or machine-readable context for automation, VI delivers both.
Cut through CVE noise with exploit-aware intelligence
Prioritize what to fix now with advanced vulnerability intelligence and real-time exploit tracking.