Coverage, validation, and intelligence-together.
FullHunt combines internet-scale discovery with continuous validation and vulnerability intelligence, so teams focus on issues that actually raise risk.
Unlike search-only data feeds or ticket-only scanners, FullHunt ties accurate asset maps to high-signal checks and exploit-aware prioritization.
It's built to integrate with your tools and your workflows-UI, APIs, or OEM-so value shows up quickly where people already work.
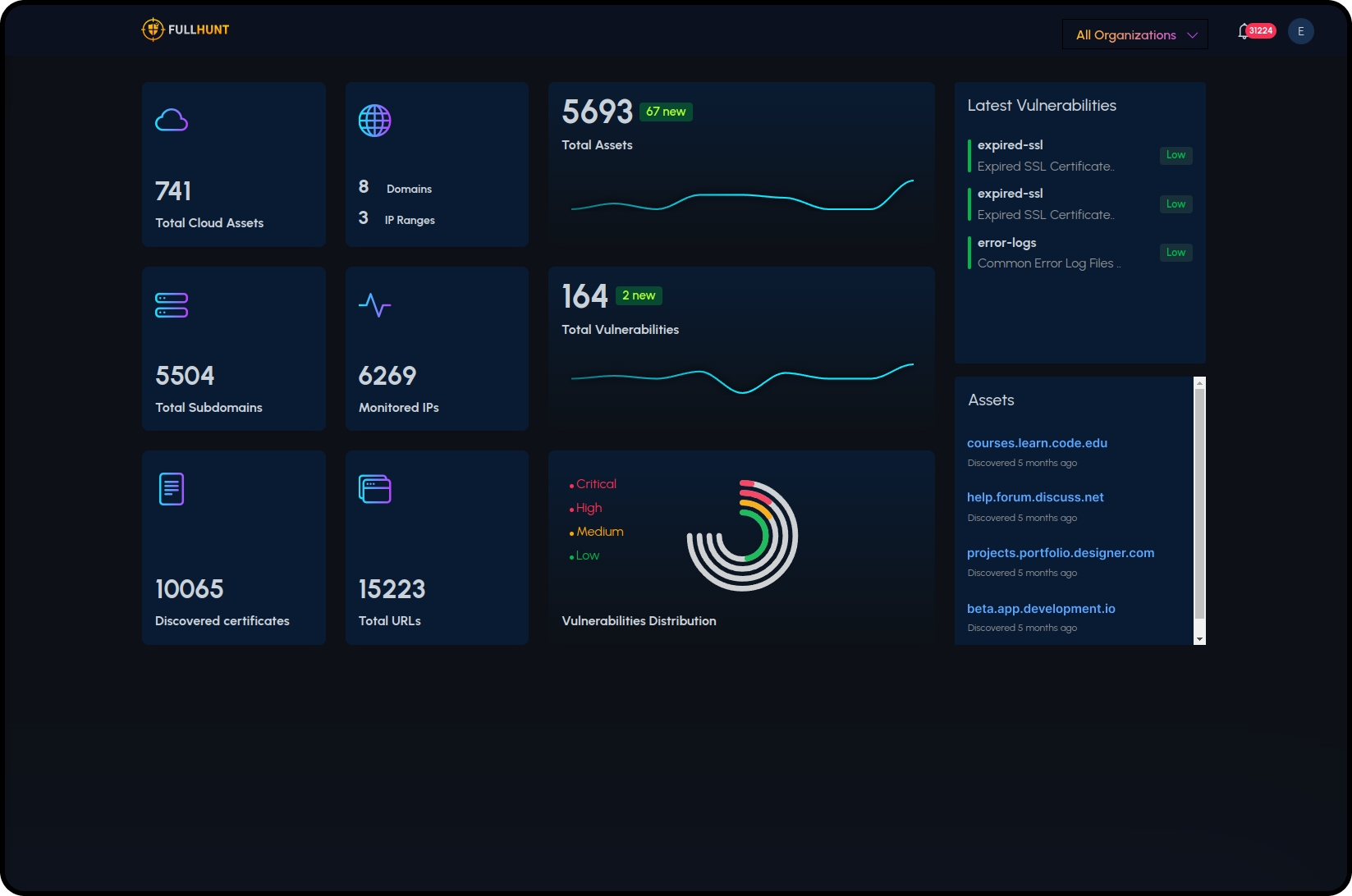
Continuously discover your attack surface and validate vulnerabilities in real-time
Constantly Evolving Intelligence
Our detection capabilities grow every day to keep pace with the evolving threat landscape
Rapidly expanding coverage; continuously updated
Growing detection library, always up-to-date
Comprehensive exploit database updated in real-time
Vulnerability Intelligence
Advanced vulnerability intelligence with curated security research and real-time exploit tracking, delivered to console and APIs

Complete Attack Surface Protection in 4 Steps
From discovery to real-time alerting, FullHunt provides continuous attack surface management that scales with your organization.
Discover
Cloud-distributed engines automatically discover and map your entire external attack surface in minutes, including domains, subdomains, IPs, and cloud assets.
Monitor
24/7 continuous monitoring tracks every change across your attack surface, detecting new assets, configuration drifts, and potential exposures in real-time.
Detect
Automated scanning identifies thousands of vulnerabilities across your assets, with runtime validation ensuring zero false positives and accurate risk assessment.
Alert
Instant notifications through your preferred channels (Slack, Teams, SIEM) whenever critical risks or exposures are identified, enabling immediate response.

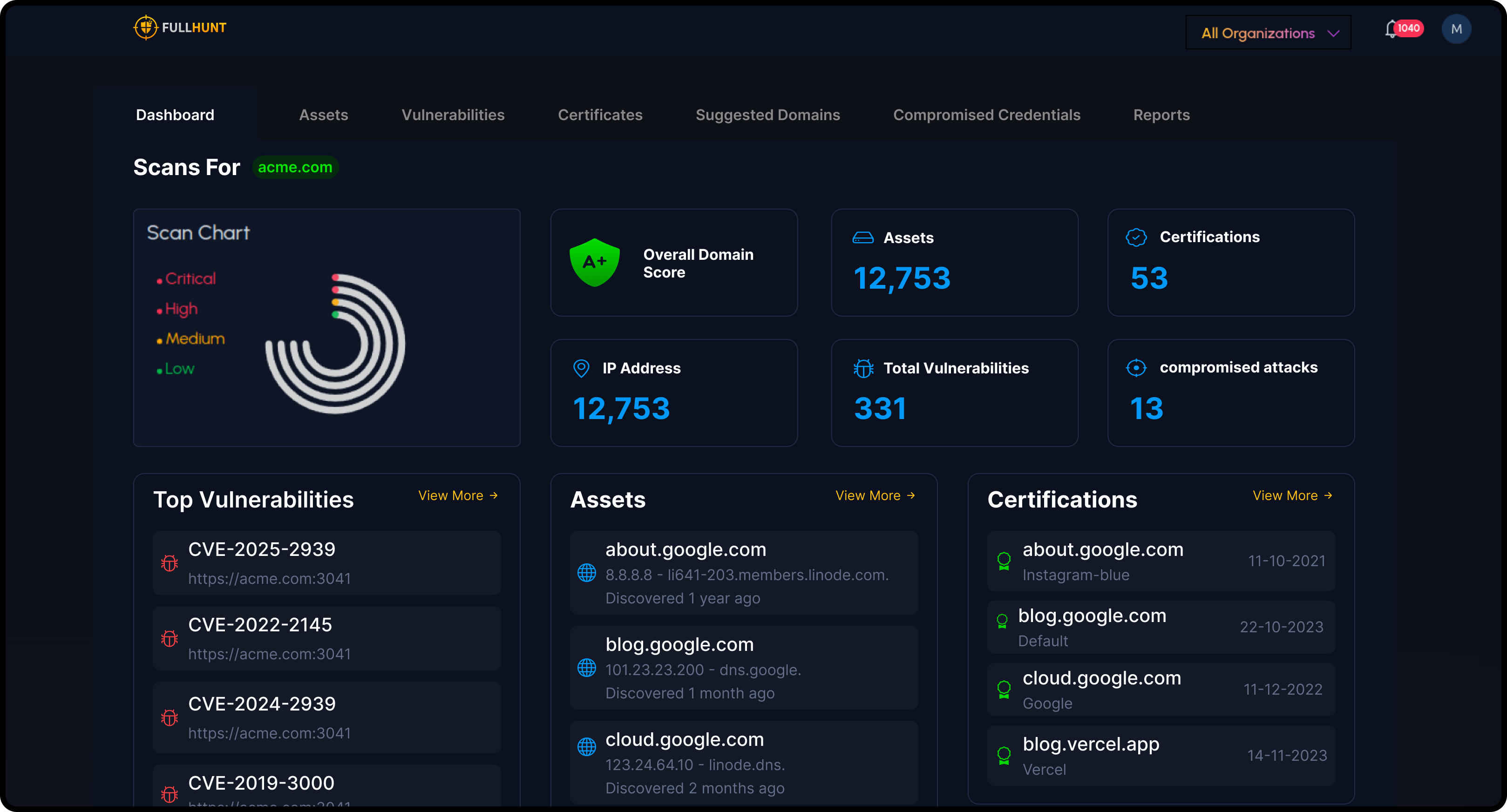
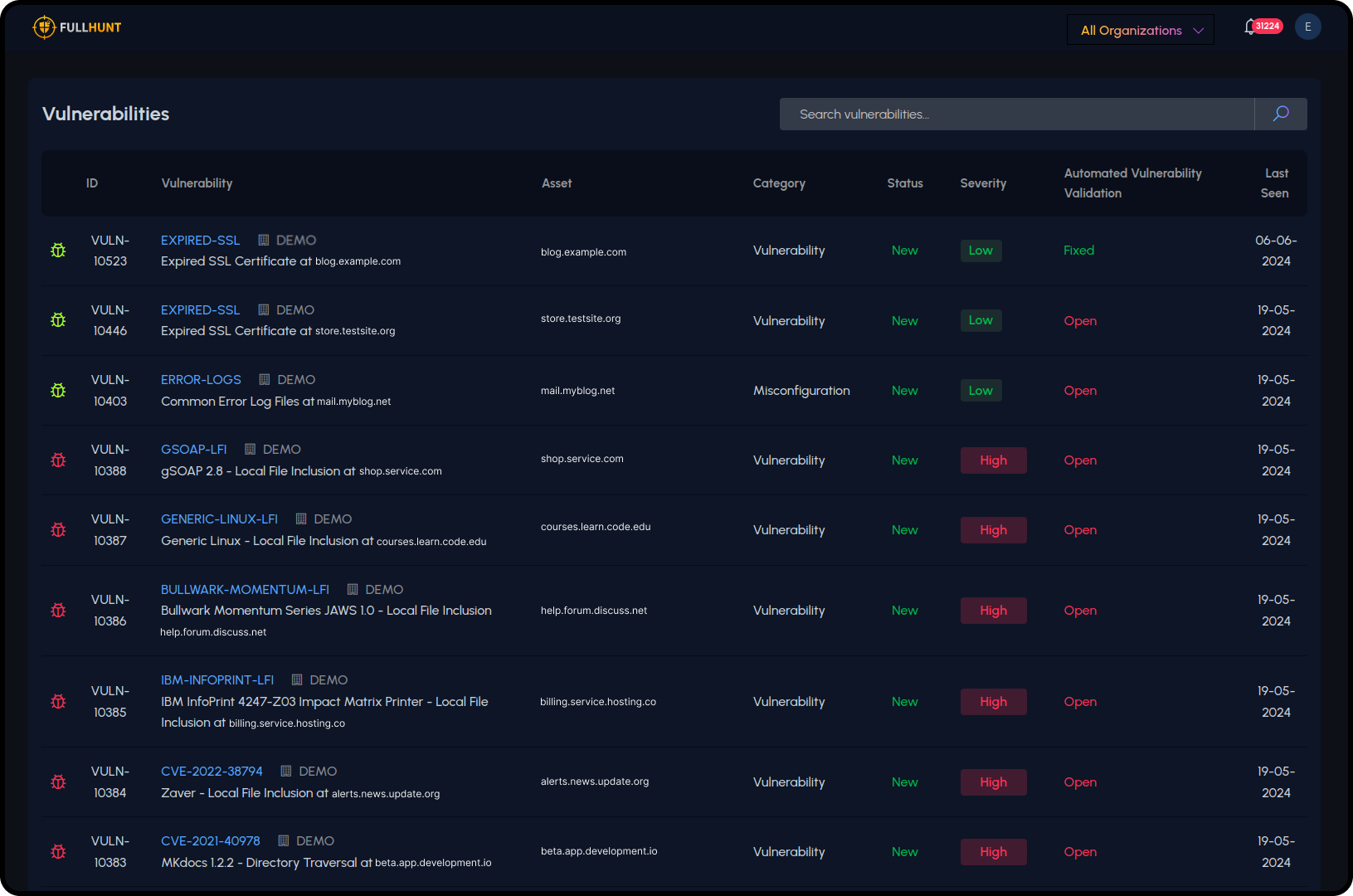
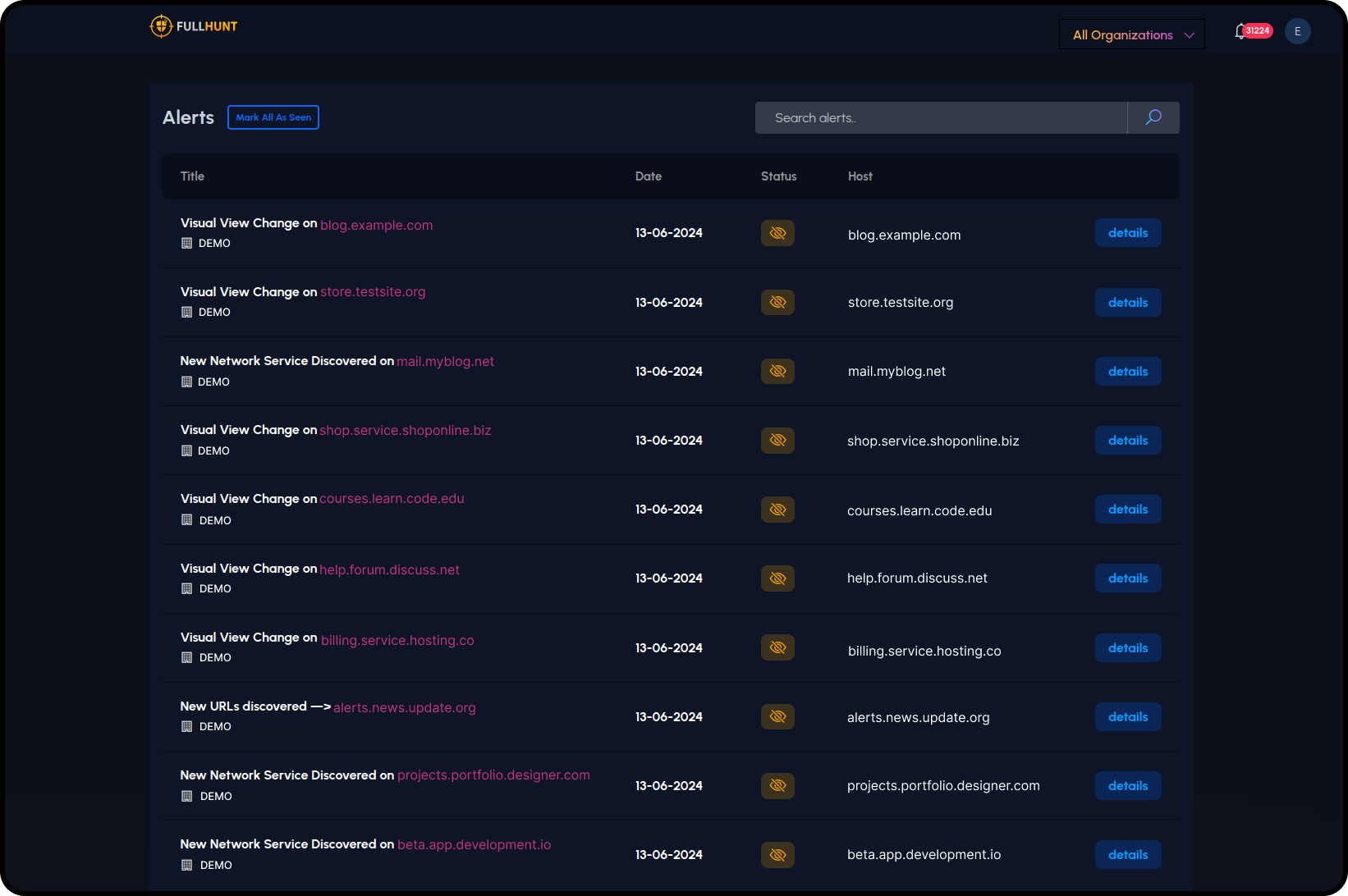

Key Differentiators
What makes FullHunt unique in the market
Continuous, Global Coverage
A live, internet-wide scanning approach keeps your data accurate every hour of every day-not point-in-time snapshots.
Exploit-Aware Prioritization
Advanced vulnerability intelligence with curated security research helps you focus on what's actually being exploited in the wild.
Built for Builders
Comprehensive APIs, detailed docs, and native integrations make it easy to automate or embed.
Shipping Velocity
Continuous innovation with major feature releases, signature expansion, and new products regularly.
How FullHunt is Different
Internet-Scale Discovery
FullHunt scans the internet continuously, mapping domains, subdomains, IPs, cloud assets, and services. Unlike tools that require you to tell them what to look for, we discover shadow IT and forgotten infrastructure automatically.
Runtime Validation
High-fidelity checks validate findings to reduce false positives. Thousands of checks run continuously, confirming actual exploitability rather than generating noisy alerts.
Vulnerability Intelligence
Findings are enriched with advanced vulnerability intelligence, curated security research, and real-time exploit tracking to help you prioritize what to fix now vs. what can wait.
Organization Attribution
Assets are automatically attributed to your organization and business units, making it easy to scope third-party vendors, subsidiaries, and internal teams.
Turnkey Integrations
Native integrations with Splunk, Cortex XSOAR, FortiSOAR, Jira, Slack, and more mean findings go straight into your existing workflows.
OEM Ready
Security vendors can white-label and embed FullHunt capabilities directly into their platforms with flexible licensing and dedicated support.
Proven Across Use Cases
Security teams use FullHunt to solve real problems
Built for Scale and Speed
Fast Onboarding
Enterprise teams operational in under 30 minutes with zero-config setup
Unified Platform
Discovery, monitoring, validation, and intelligence work together seamlessly
Enterprise-Grade
SSO, RBAC, data encryption, and compliance controls built-in
Choose Your Path to Value
Get started with the option that fits your needs
Why FullHunt Stands Out
Continuous, Global Coverage
A live, internet-wide scanning approach keeps your data accurate every hour of every day.
Zero False Positives
Rigorously verified findings mean your team only sees genuine risks.
Executive-Friendly Dashboards & Reports
Big-picture clarity for CISOs, with technical detail available for security engineers.
Integration-Ready
Easily align with existing workflows (SIEM, SOAR, ticketing systems) for real-time alerts and data sharing.
Lightning-Fast Onboarding
See your entire internet-facing footprint in seconds, not days or weeks.
FullHunt doesn't just discover your assets; it defends them. We bring together continuous discovery, automated vulnerability validation, and streamlined remediation workflows into one unified platform.
Ready to see it in action?
Join security teams using FullHunt to discover, monitor, and secure their external infrastructure.
