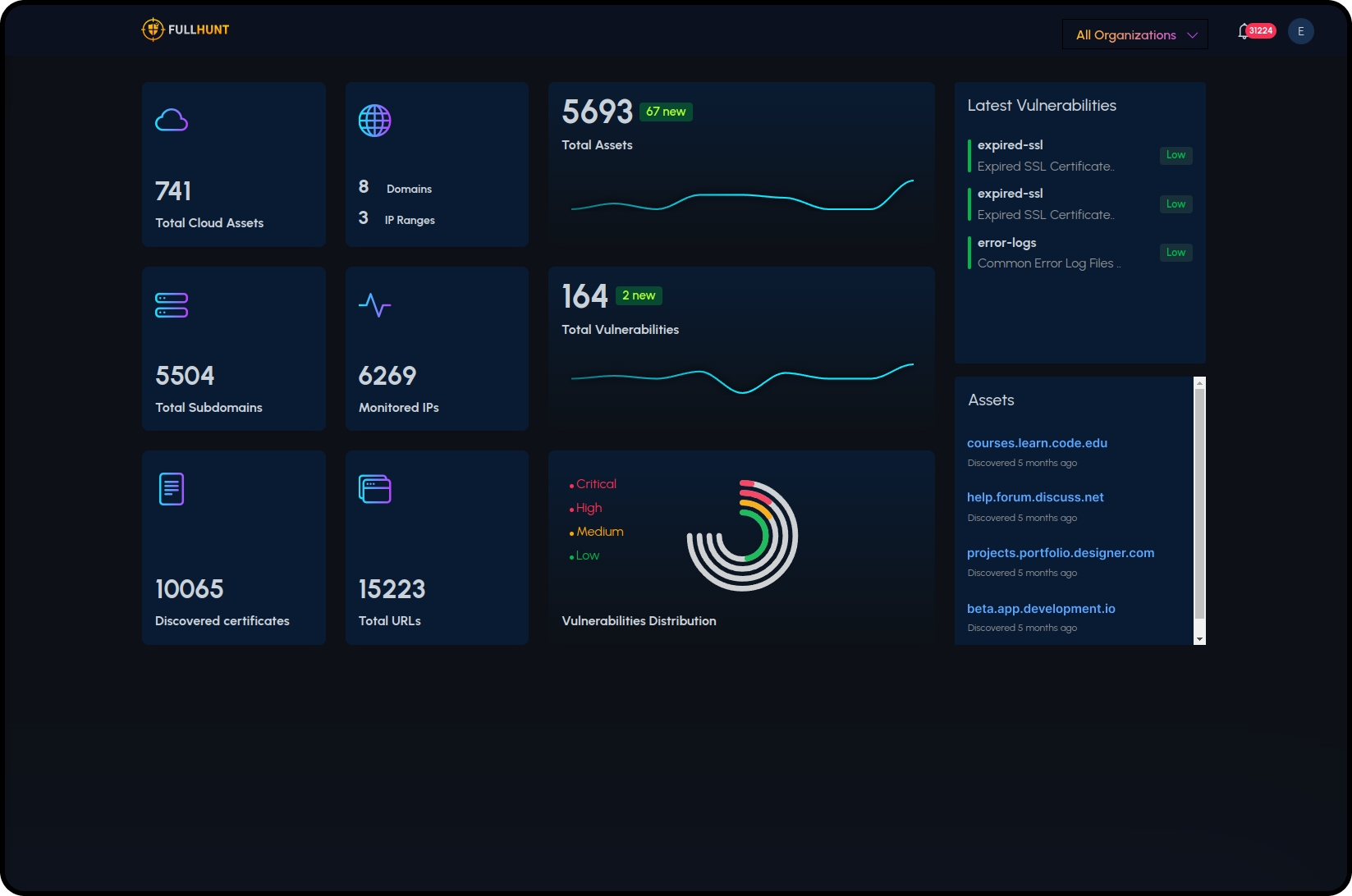
Complete Attack Surface Management
Discover, monitor, validate, and integrate: the continuous cycle that keeps your external attack surface under control, with zero agents and minimal deployment effort.
The FullHunt Workflow
A continuous cycle of discovery, monitoring, validation, and integration that keeps your external attack surface under control, with zero agents and minimal deployment.
Discover
Build complete external asset visibility

FullHunt continuously maps your internet-facing infrastructure: domains, subdomains, IPs, cloud services, and technologies. Discovery runs at internet scale using passive data sources and active reconnaissance, uncovering shadow IT and forgotten assets automatically.
Key Capabilities:
- Automated subdomain enumeration
- Multi-cloud asset discovery (AWS, Azure, GCP, Alibaba, Oracle)
- Technology & product fingerprinting
- Organization and ownership attribution
Monitor
Track changes and drift 24/7

Real-time change detection surfaces new services, configuration drift, and exposure changes as they happen. Instant alerts notify security teams of risky changes before they escalate into security incidents.
Key Capabilities:
- Real-time change notifications and alerts
- New asset and service detection
- Configuration drift tracking
- Technology stack monitoring
Validate
Confirm real exploitability, eliminate noise

High-fidelity, runtime-validated scanning confirms actual exploitability with zero false positives. Findings are enriched with EPSS scores, KEV data, curated security research, and real-time exploit tracking to help teams prioritize what matters most.
Key Capabilities:
- Thousands of vulnerability checks (4,000+)
- Runtime validation for zero false positives
- EPSS & KEV enrichment for prioritization
- Public exploit correlation and tracking
Integrate
Push findings into your workflows
Native integrations and comprehensive APIs push prioritized findings into existing security workflows. Issues are routed automatically to the right teams, assignments are clear, and retests happen on schedule with no manual exports required.
Key Capabilities:
- SIEM/SOAR integrations (Splunk, XSOAR, FortiSOAR, Mindflow)
- Ticketing systems (Jira, ServiceNow)
- Chat & collaboration (Slack, Microsoft Teams)
- Webhooks & REST APIs for custom workflows
Why This Approach Works
The continuous 4-step cycle enables true exposure management, not just discovery or scanning alone
Continuous, Not Point-in-Time
Unlike periodic scans that leave gaps, FullHunt runs continuously 24/7 so you catch changes as they happen with zero blind spots between assessments.
High Signal, Low Noise
Runtime validation and exploit-aware prioritization eliminate 90% of false positives, so your teams focus on real, exploitable issues that matter.
Fits Your Workflow
Native integrations mean findings automatically flow into tools your team already uses. No new platforms to learn or context switching required.
Enterprise-Ready from Day One
Designed for enterprise security teams with the scale, speed, and simplicity you need
SSO & RBAC
Enterprise authentication and role-based access control built-in for secure team management
Fast Onboarding
Operational in less than 30 minutes with zero infrastructure deployment required
Zero Agents
Agentless, outside-in visibility with no performance impact on your infrastructure
Infinite Scale
From startups to Fortune 500 companies, monitor up to 400K assets seamlessly
What Makes FullHunt Different
Unlike point-in-time scanners or search-only tools, FullHunt combines discovery, monitoring, validation, and integration into one continuous platform
Internet-Scale Discovery
We don't just scan what you tell us to scan. FullHunt automatically discovers shadow IT, forgotten infrastructure, and multi-cloud assets, ensuring complete coverage of your external footprint without manual inventory management.
Zero False Positives
High-fidelity runtime validation confirms actual exploitability. Thousands of checks run continuously, verifying real vulnerabilities instead of generating noisy, unactionable alerts that waste your team's time.
Exploit-Aware Intelligence
Every finding is enriched with EPSS probability scores, KEV tracking, curated security research, and real-time exploit correlation. This helps you prioritize what to fix now versus what can wait.
Native Integrations
Push prioritized findings directly into Splunk, Cortex XSOAR, FortiSOAR, Mindflow, Jira, ServiceNow, Slack, Teams, and more. Automate workflows without manual exports or context switching.
Platform Capabilities in Detail
Use FullHunt's advanced suite of tools to discover, monitor, and protect your assets. From continuous vulnerability scanning to real-time threat detection and comprehensive third-party risk management, FullHunt is here for you.

Asset Discovery
Discover all your external assets, including shadow-IT and unknown assets, within seconds. FullHunt's advanced discovery capabilities ensure complete visibility of your attack surface.


Asset Monitor
Continuously monitor your assets for any changes or exposures. FullHunt provides real-time profiling and alerts, always keeping you informed about your security posture.
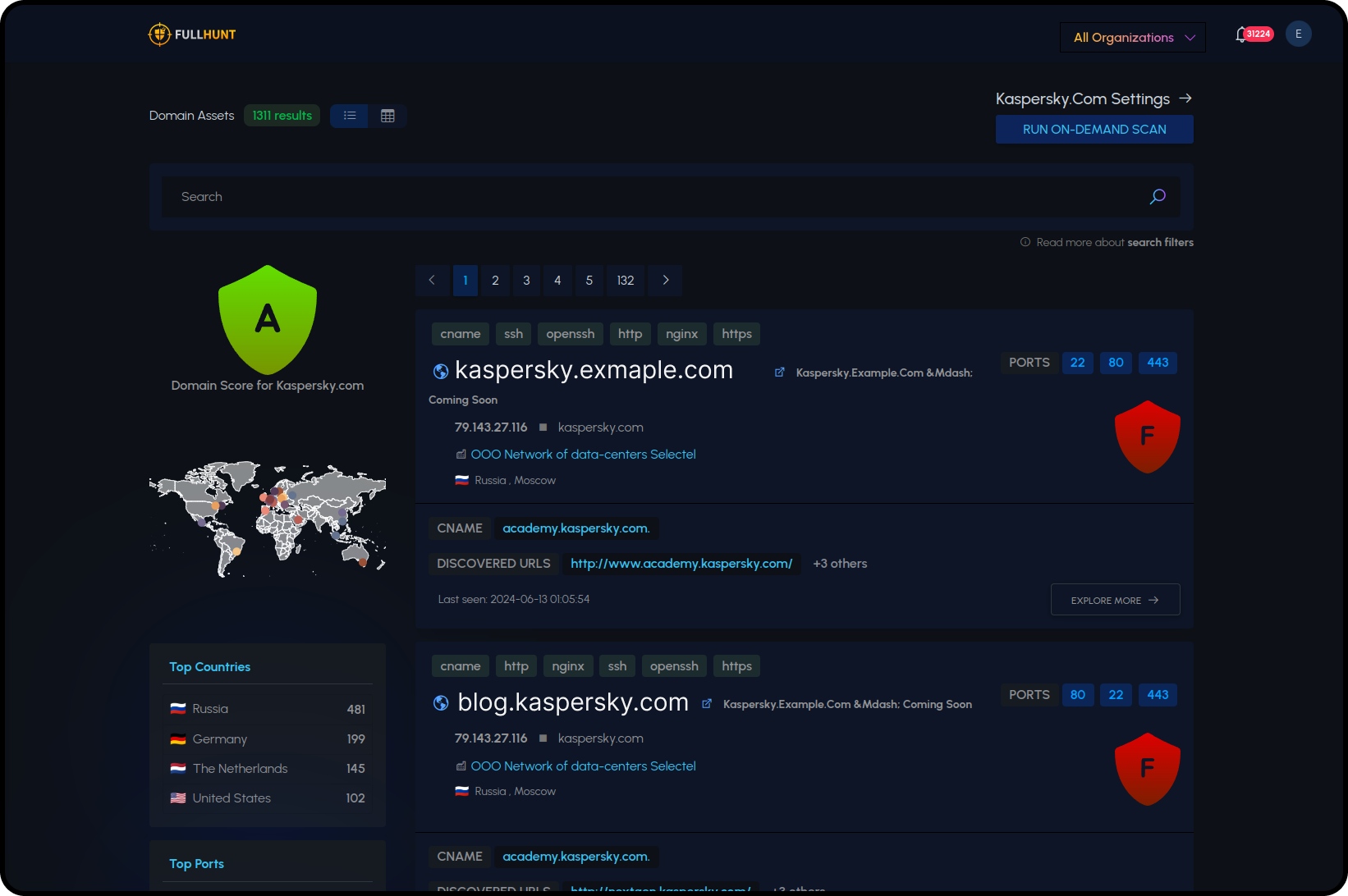

Vulnerability Scanning
Perform continuous security scanning across all your assets with FullHunt Owl. Our platform automatically identifies and reports vulnerabilities, enabling prompt action to mitigate risks.
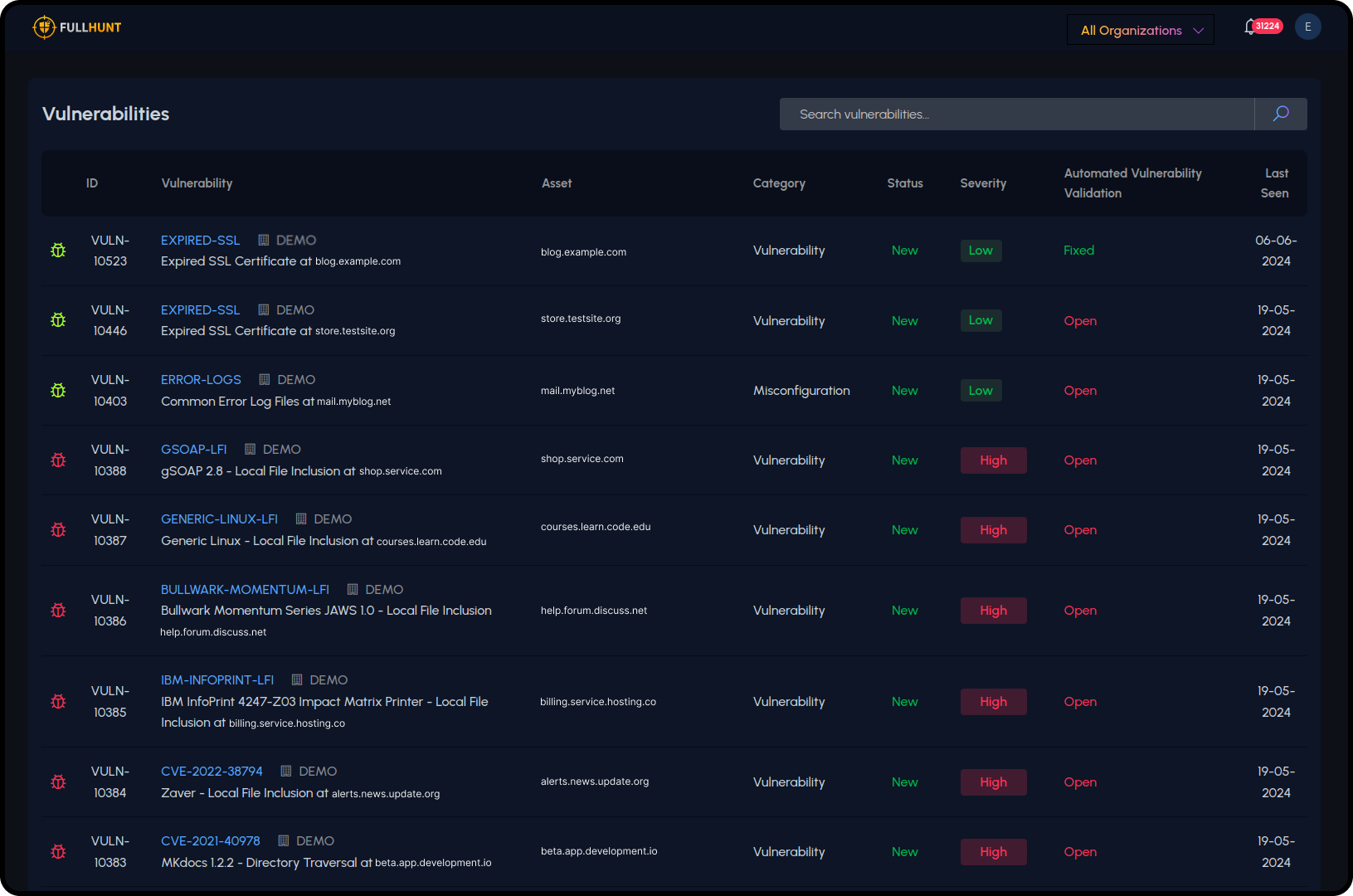

Asset Database
Maintain a comprehensive, automated inventory of your external assets. Our platform keeps an up-to-date record, eliminating the need for manual tracking and ensuring accurate asset management.


Third-Party Risk
Identify and manage risks associated with third-party vendors and subsidiaries. FullHunt's advanced monitoring and scanning tools provide comprehensive assessments to maintain a robust security posture.
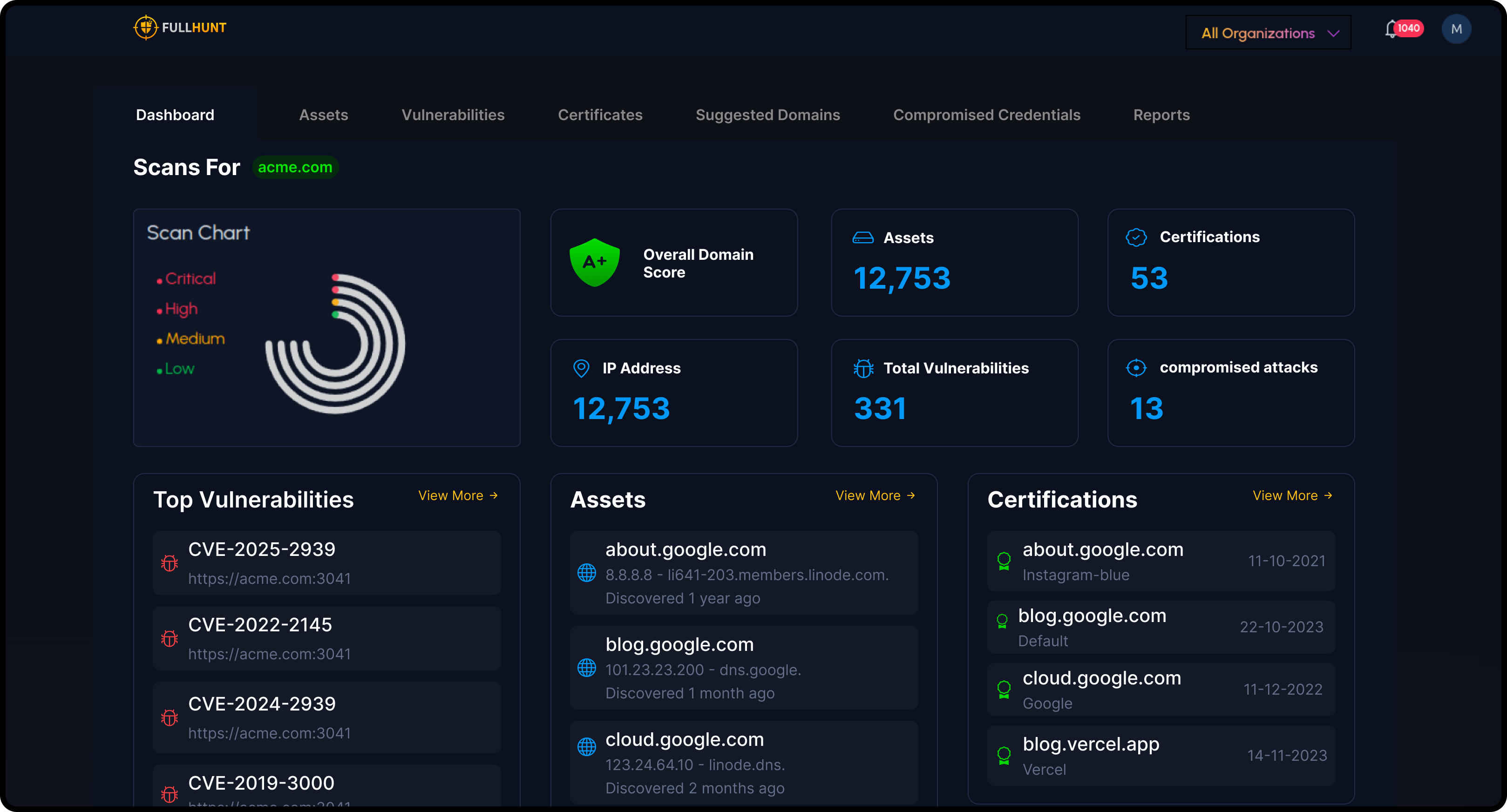

Vulnerability Prioritization
Focus on the most critical issues first with FullHunt's advanced analytics. We help you prioritize vulnerabilities based on their risk and impact, optimizing your remediation efforts.


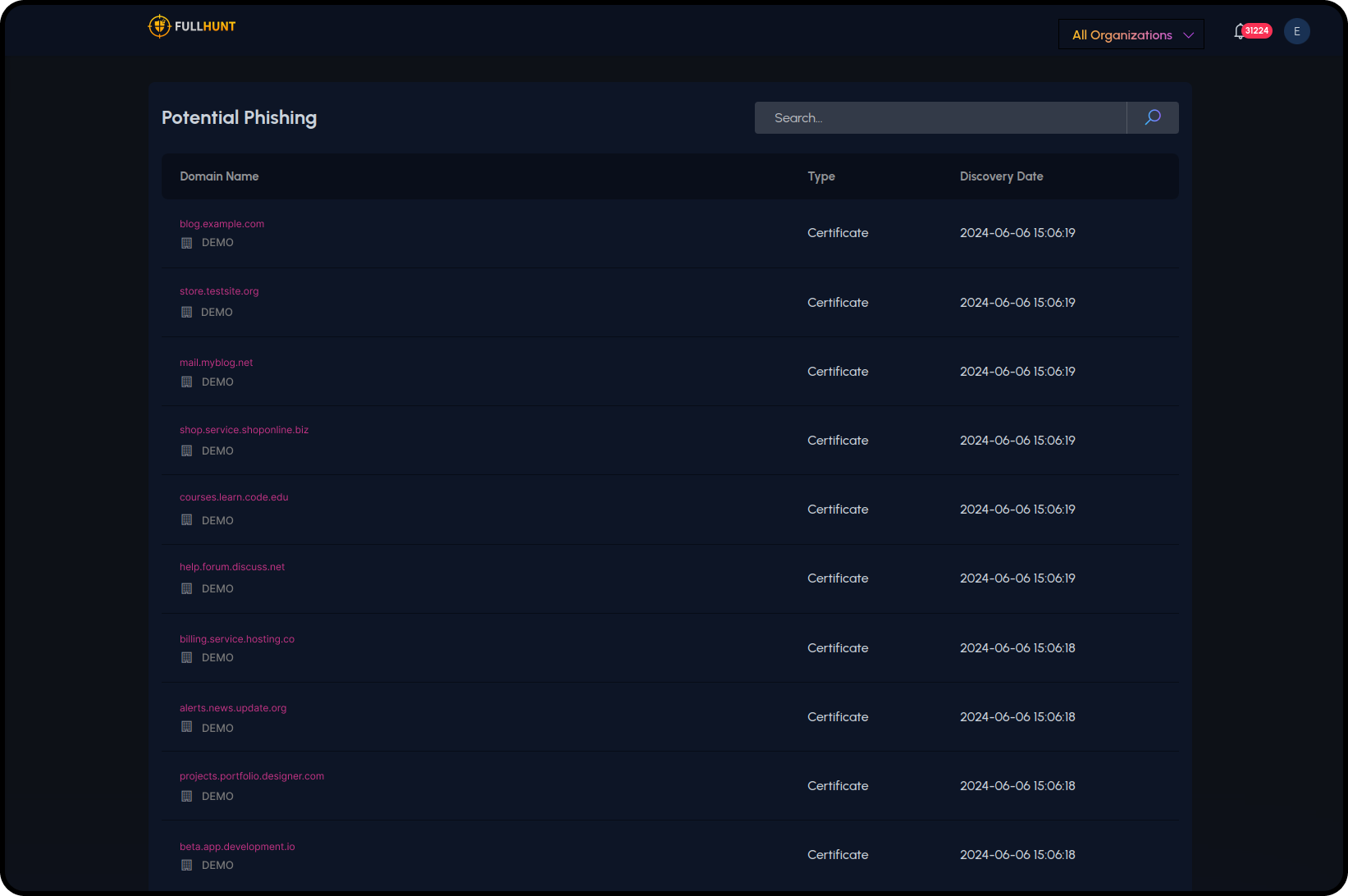
Potential Phishing & Typosquatting
Detect and mitigate phishing and typosquatting threats with continuous monitoring. FullHunt identifies suspicious activities, allowing you to take preventive measures against cyberattacks.

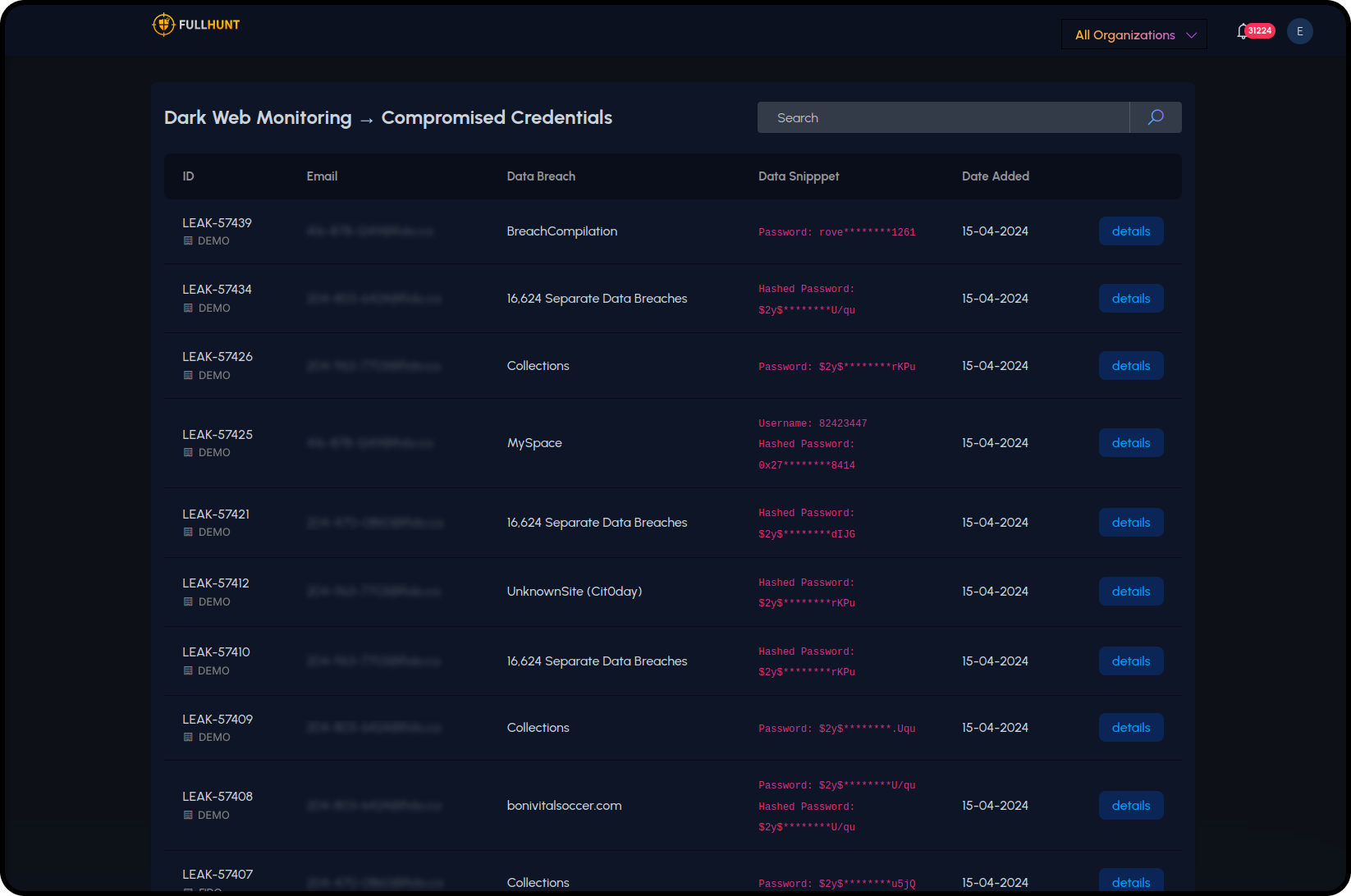
Dark Web Monitoring
Run continuous scans on the dark web to alert your organization about potential risks. FullHunt helps you stay ahead of emerging threats by identifying and mitigating dark web exposures.

FullHunt Owl
FullHunt Owl is an automated discovery and vulnerability scanning product by FullHunt. It provides companies with automated discovery and high-signal vulnerability scanning for subsidiaries, third-party vendors, and one-time scans.


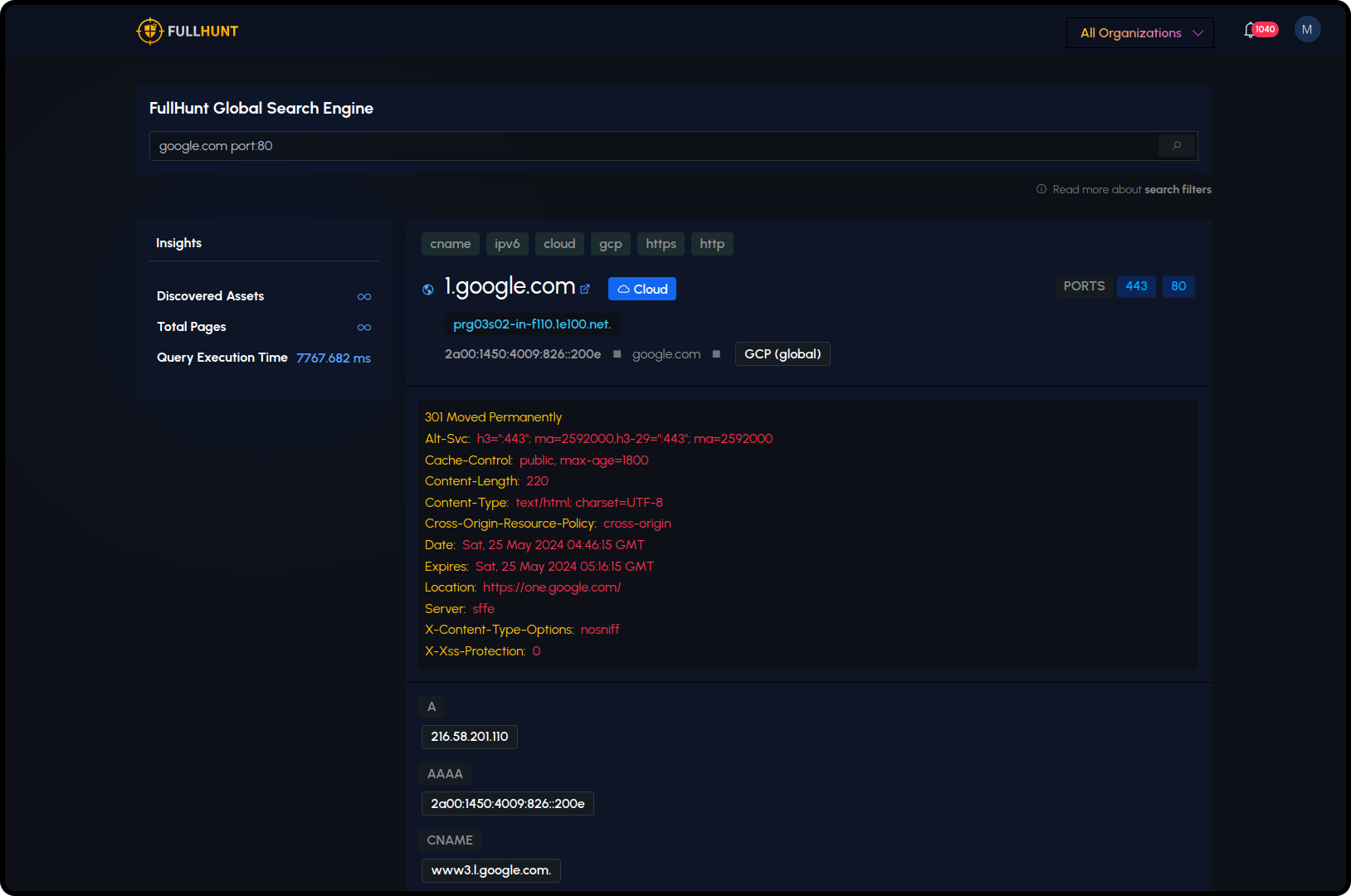
FullHunt Global Search
FullHunt Global Search scans the external attack surface of an entire nation and identifies vulnerable websites, servers, databases, and VPNs using a blazing-fast API capability. Available to government agencies and CERTs.
Utilize FullHunt Global Search to analyze and monitor internet-connected assets worldwide. Gain insights into the global threat landscape and take proactive measures to protect your organization.
FullHunt Data Intelligence
FullHunt Data Intelligence provides access to search across the FullHunt database with state-of-the-art capabilities to identify services that match particular patterns, and uncover new attack surfaces unknown to your organization. Organizations can use the APIs for large-scale investigations and threat hunting.

See How It Works in Your Environment
Experience the complete FullHunt workflow in action. Discover your attack surface, monitor changes, validate vulnerabilities, and integrate with your security stack, all in one demo.
- Live platform walkthrough
- Use your own domains
- No infrastructure needed